Security continues to be a major issue within the crypto space.
Although Blockchains are designed for optimal security because of their decentralized nature, this has not prevented the users and institutions operating on these Blockchains from being exposed to hackers.
From Mt.Gox exchange ($473 million hacked), to Bitfinex ($72 million hacked), and most recently, Crypto Youtuber Ian Balina ($2 million hacked).
It’s clear that users and exchanges are still very exposed.
Fortunately, a new Blockchain company called Sentinel Protocol promises a solution to secure our exchanges and funds.
What is Sentinel Protocol?
Sentinel Protocol is offering a cyber security ecosystem that leverages the collective intelligence of cyber security specialists, as well as advanced technologies like machine learning and sandboxing to help crypto traders and exchanges protect their crypto currencies.
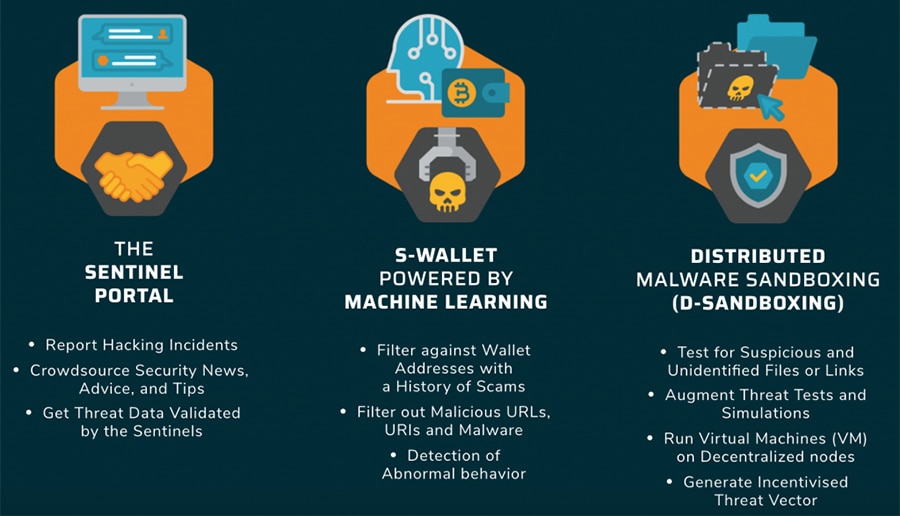 Image via sentinelprotocol.io
Image via sentinelprotocol.ioIt works by providing a threat reputation database, which contains security intelligence information like the addresses of confirmed dangerous wallets belonging to hackers, or malicious URL's.
The database sits on the Blockchain and is connected to API's.
Exchanges and other organizations can use these API's in order to receive an alert or block an action whenever they encounter any of these malicious URLs or wallet addresses.
Sentinel protocol provides 3 main security features: The Sentinel Portal or Threat reputation database (TDRB), Machine-learning engine integrated security wallet (S-wallet), and a distributed malware analysis sandbox (D-Sandbox).
Threat Reputation Database (TRDB)
The threat reputation database is designed to offer a decentralized source of shared knowledge amongst security vendors. This database is provided as an API that individuals and organizations can connect to.
Traditionally, security vendors would compile information by themselves and store them in the centralized databases of their respective organizations.
This lead to security blind spots due to the lack of complete information, as well as the centralization of vital data creating a single point of failure (NSA’s hacking by Russian state hackers in October 2017 is an example of this flaw).
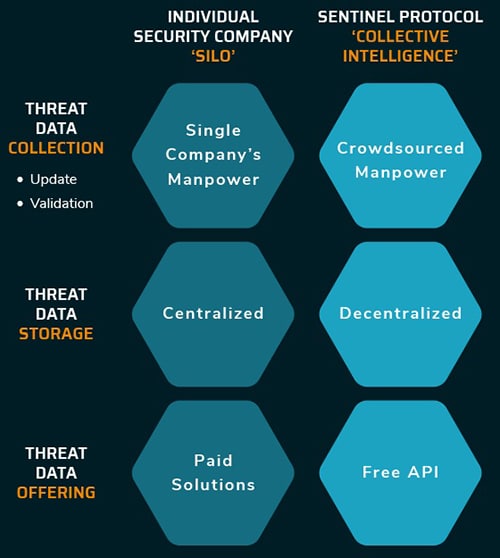 Sentinel Protocol TRDB
Sentinel Protocol TRDBTRDB uses a token incentive scheme that encourages vendors to contribute to an ever-expanding threat database containing hacker’s wallet addresses, malicious URI’s, phishing addresses, malware hashes, and more.
Submissions are validated based on group consensus and feedback from participants using the Delegate proof of stake method.
Only security experts can update TRDB, however, general users can also participate by auto reporting or manual reporting.
Auto reporting allows Sentinel Protocols machine learning based security wallet to automatically detect unknown threats the user comes across while connected to the TDRB API.
When a threat is identified, it is sent to the database. Manual reporting requires the user to report the risk information themselves, which is then validated by the security community afterwords.
S-Wallets
S- Wallets can be held by individuals or institutions to store their crypto currencies with enhanced security.
The S-Wallet uses machine learning to anticipate incoming security threats based on information gathered from the threat reputation database. The wallet operates like anti- virus software, except it doesn’t have to wait to receive updates from a centralized server. It can be more proactive in its detection based on analysis of threat tendencies and history gathered from the TRDB.
The S-Wallet is especially effective against Ransom ware threats, and provides filters for Crypto currency wallet addresses, URL/URI’s and other forms of Data.
The machine learning technology also enables Sentinel Protocols Fraud Detection System to identify transactions that are reported for misuse or stolen.
D-Sandbox
Sandbox is a security mechanism that isolates untested and unverified programs. These programs are isolated away from the main application and into a testing environment so that potential threats can be analyzed and submitted to collective intelligence via a ticket system.
These 3 features of Sentinel Protocol are overseen by the ‘Sentinels’, a group of security experts, individuals and organizations who serve to validate hacking claims, analyze the root cause of a threat, and update the TRDB.
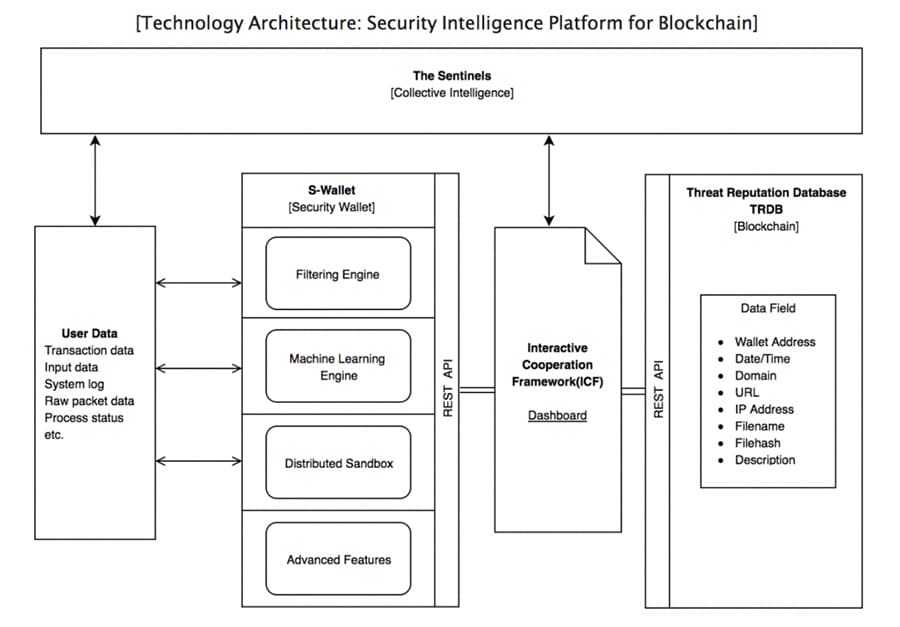 Image via Sentinel Whitepaper
Image via Sentinel WhitepaperSentinel Protocol Token Economy
Just like how black hat hackers are incentivized by money to perform malicious activities, Sentinel protocol aims to create an ecosystem where white hat hackers (or Sentinels) can earn money by contributing to the security intelligence of the ecosystem.
Sentinels earn ‘sentinel points’ for their contributions, and these points can later be converted to crypto tokens called UPP (Uppsala) Tokens.
Sentinel points are added up as a reputation score that evaluates how much a Sentinel has helped a hacking victim, or contributed to the TRDB.
Users can make indirect contributions and earn sentinel points by creating or translating articles to alert the community about cyber-security threats.
UPP tokens are the currency used to pay for security features within the Sentinel Protocol ecosystem.
The threat detection database as well as API integration come free, while users have to pay UPP tokens to use more advanced features like Machine Learning-based anomaly detection or Distributed-sandboxing.
Team
Sentinel Protocol gathers one of the most experienced teams in the Blockchain space. Their combined expertize in cyber security spans decades, and involved working for major corporations as well as Governments.

Patrick Kim – Founder and CEO
Patrick came up with the idea for Sentinel Protocol when in 2016, 7,218 Ether (around $70,000 at the time) was stolen from his wallet as a result of a hack.
He took this very unfortunate incident and turned it into a business opportunity by starting Uppsala foundation, which Sentinel Protocol is under.
Patrick brings 10 years of experience with network security and system architecture at Palo Alto Networks and Fortinet.
Before this, he was Koreas chief technology consultant at Darktrace, and AI focused global security company. He consulted the government and large corporations including Korea Cyber Defense and Samsung.
Hae-Min Park - Business Operations
Hae leads the business operations of Sentinel Protocol. He has over ten years of IT security experience, specializing in database architecture, web application firewall (two patents), fin-tech security, and machine learning.
Prior to Sentinel Protocol, Hae designed the DB architecture of the corporate banking system at KB Bank, and led global business operations in Korea at F5 Networks and Darktrace.
John Kirch – Chief Evangelist
John has over 25 years of international experience in Asia’s high-tech industry. He specializes in next-generation software solutions to address the needs of organizations throughout the key markets across the Asia Pacific region, particularly in Japan.
Prior to Sentinel Protocol, John held senior roles with several leading technology companies including WatchGuard Technologies, Softbank, CyberGuard, and Darktrace.
Pros / Strengths
- Highly experienced cyber security team
- First mover advantage in Crypto security
- Sentinel has a very utility focused Token structure. They have well-designed incentive structures to create the best ecosystem for cyber security.
- Sentinel protocol began working on the security problem in 2016, and is one of a very small group of companies focused specifically on Blockchain security today
Cons / Weaknesses
- The success of Sentinel protocol is very reliant on external assistance. I’m not sure if tokens will be enough to incentivize cyber security experts to collaborate with each other, especially if they compare what they will earn as part of the sentinel network versus working exclusively for one Blockchain (or non-Blockchain) company.
- The money individuals or institutions pay to get access to exclusive security features is a big factor preventing the best security experts from collaborating with each other today. There’s also the issue of secrecy between nations, which may prevent many cyber security experts who work for Governments from contributing.
ICO Specifics
Sentinel protocols Token Pre Sale starts on May 23.
Their public sale starts on May 27th and ends on June 10th. The company is looking to raise $32,900,000, and have already raised $23,294,012.
- Ticker: UPP
- Token type: ERC20 (though the company plans to migrate to ICON once it is more stable)
- ICO Token Price: 1 UPP = 0.14 USD (0.00020000 ETH)
- Fundraising Goal: 32,900,000 USD (48,000 ETH)
- Sold on pre-sale: 15,400,000 USD (30% BONUS (6 MONTHS LOCK-UP))
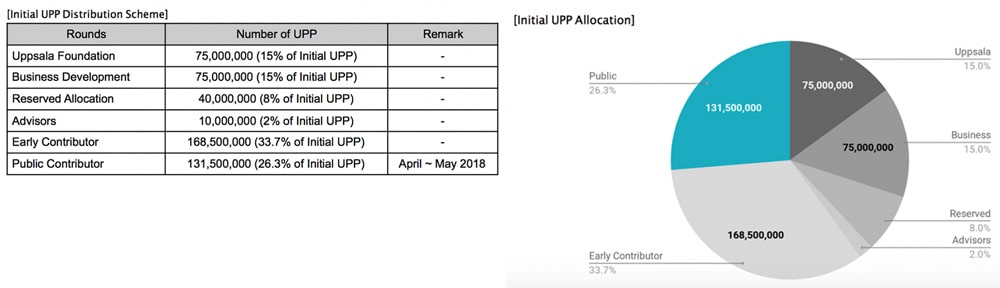
- Total Tokens: 500,000,000 UPP
- Available for Token Sale: 60% (300,000,000 UPP)
Presale Requirements
Whitelisted [concluded]
KYC verified (Submission date: April 25th – May 5th. Result date: May 21st)
Min/Max Contribution: 30-300 ETH
Crowd sale Requirements
KYC verified (Submission date: April 25th – May 12th. Result date: May 25th)
Min/Max Contribution: 0.5-10 ETH
Conclusion
Sentinel protocol is offering a service that solves a critical problem within the crypto community – security.
As more exchanges are launched and more crypto users emerge, security will only become a bigger issue.
By becoming one of the first Blockchains to focus entirely on security, Sentinel protocol is well positioned to be a relevant player in this space for a long time.
The company has wisely chosen not to go the route of conventional marketing, and is instead focused on bringing real world cyber-security experts to Sentinel Protocol, and establishing partnerships with exchanges, wallets and payment services.
They may face some initial challenges recruiting the best security experts to the network. These players are already in high demand and will be dealing with competing interests in the real world.
However, overtime we do believe Sentinel protocol will begin to achieve a network effect as institutional investors enter the space and demand higher levels of security to protect their funds.