Could Your Ledger Nano be Susceptible to a Man in the Middle Attack?
Ledger Nano is without a doubt the most popular hardware wallet currently on the market. They have sold well over 1 million devices to security conscious cryptocurrency Hodlers around the world.
However, it has recently been reported that the wallet could be susceptible to a man-in-the-middle (MITM) attack. There have been no reports of this exploit actually being used but given the amount of ledger nano's globally, it is still troubling.

Hence, in order to take a step ahead of any potential exploit of their user's funds, the Ledger team released their guidance on how one could make sure that they do not fall victim to this attack vector.
Before we take a look at the potential exploit, it is necessary for us to understand some fundamentals.
Harware Wallets and MITM Attacks
Hardware wallets are viewed as one of the safest ways to store large amounts of coins and keep them out of the hands of hackers. These are an extension of cold storage options that are "airgapped". Airgapped implies that the coins are stored somewhere where they are not connected to the internet.
The hardware wallet will store the most important data (private key) on the device and make sure that it cannot be accessed from outside forces. The only time that the wallet will ever interact with the network is when you have to send the coins and connect it to your PC.
Man-in-the-Middle attacks are those when an attacker will insert themselves between you and another network node or server. They will monitor your traffic and try and extract important information that can be used to compromise you.
What is the Attack Vector?
As mentioned, the only time that a hardware wallet has to be connected to the web is when you are sending funds. Although this was thought to still be extremely secure, the researchers have discovered the vulnerability.
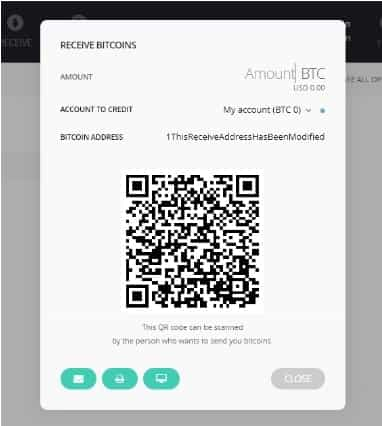
As explained in the report, the Ledger wallets will generate the receive address using JavaScript that will operate on the host PC. Hence, if there was some malware that was on the host machine, it could change the wallet address by altering the Ledger code.
This can be seen in the image on the right as the individual is electing to receive Bitcoin. The address has been changed and the receiver may be duped into sending to the wrong address. Moreover, given that the wallet structure usually changes these addresses, they may not know this.
Why is This So Dangerous?
Although this would still require a hacker to place Malware on your PC, the researchers pointed out that altering this code for the wallet interface is not that complicated for the Malware to accomplish.
The JavaScript files are stored in AppData folder which does not require special user privileges to access. There is also no checks that are done by ledger to make sure that the source files have not being tampered with prior to execution.
Given how simple it is to access the files and change a line of JavaScript code, the researchers have pointed out that all that would be required by the Malware would be to insert about 10 lines of Python code.
Similarly, this could be quite a profitable attack vector for those who are new to the cryptocurrency game. As soon as someone has purchased all of their coins on an exchange, they are likely to send it to their wallets. This will result in the hackers being able to harvest their large initial portfolios.
Lastly, the attack works in such a way that it is able to change the QR code as well. The address is changed in the source code prior to the generation of the QR code. Hence, they will both correspond to the incorrect address.
Potential Mitigation Measures
The researchers had some suggestions about how one could avoid falling victim to the attack if they were indeed infected. One of them could be an undocumented feature that exists for the Bitcoin wallet in ledger.
This is a small button at the bottom of the screen that will allow the user to monitor the wallet address on the ledger screen itself. This way, they can confirm that the address that correctly corresponds to the wallet is indeed being correctly displayed on the PC screen.
This is also something that was suggested by the ledger team in a tweet as they responded to the disclosure.
The researchers pointed out that this monitor phase is not something that is part of the default send process and hence the Ledger developers could make it mandatory. Unfortunately, this is only available on the Bitcoin app of Ledger.
Implications for Ledger?
While this exploit has not being used yet, it is still quite an alarming development for the foremost hardware developer in the world. There must be billions of crypto wealth that is stored on these hardware wallets.
Although one can argue that this would still have to be Malware on the user's machine, the notion that one can so easily change the Ledger code is disturbing. Moreover, Ledger has always prided itself on keeping your coins completely secure irrespective of what lies on the host machine.
It is important to note, however, that leaving your coins on a ledger wallet is still greatly safer than leaving it on an exchange or on a desktop wallet. This is not a flaw in the ledger device itself but merely an exploit vector on the user interface with the desktop app.
Hence, as long as you are able to make sure that the address that is being presented to you on your PC is the same one that is stored on the hardware wallet, then you should be safe.
Featured Image via Fotolia
Disclaimer: These are the writer’s opinions and should not be considered investment advice. Readers should do their own research.