The Massive Undercover Mining Operation you Have Never Heard About
One of the biggest cryptocurrency mining operations has just been discovered. Spanning across the globe to numerous computers, the miners have been able to generate a hefty $3.4m in revenue.
The mining operation in question is actually an exploitation by a hacker. The threat actor made use of a critical vulnerability in Jenkins servers to install software that mines Monero, the privacy conscious cryptocurrency.
The existence of the mining operation was first discovered by researchers at check point research. Apart from giving the operator a great deal of elicit XMR, the attack will also slow the servers and possibly also issue a Denial of Service (DoS) attack.
Let's take a deeper look into this anonymous miner.
Critical Vulnerabilities
Unlike many other Monero mining exploits that make use of malware and compromised websites, the Jenkins exploit makes use of a critical vulnerability. These are also termed zero day exploits.
The undercover miner has been operating for the past 18 months and has previously made use of Windows vulnerabilities. They used these vulnerabilities to remotely download Monero mining software that would operate in the background.
Hijacking the processing power of these Windows machines was able to generate the miner 10,829 XMR which is just over $3m. The hacker, which the researchers claim is of "Chinese origin" has now moved on to exploit the vulnerability in the Jenkins server.
The vulnerability in question exists on the Jenkins Continuous Integration m(JCI) server software. More technically known as CVE-2017-1000353, the vulnerability stems from the Java deserialization and a lack of object validation.
The hacker was able to exploit this vulnerability by sending carefully crafted requests to the server. He will also then include two main objects one of which will be the "command object". The latter contains the miner payload which then executes PowerShell code.
Part XMRig Part RAT
The mining operation makes use of a hybrid version of the XMRig mining software and a Remote Access Trojan (RAT). The researchers claimed that although the miner can operate on several different machines, most of the victims appear to be personal computers. They also noted that
With every campaign, the malware has gone through several updates and the mining pool used to transfer the profits is also changed
The mining operation is also well managed and makes use of rotations to several different mining pools. However, most likely out of convenience the hacker makes use of only one Monero wallet. The wallet in question is in the below image with mining rewards still streaming in.
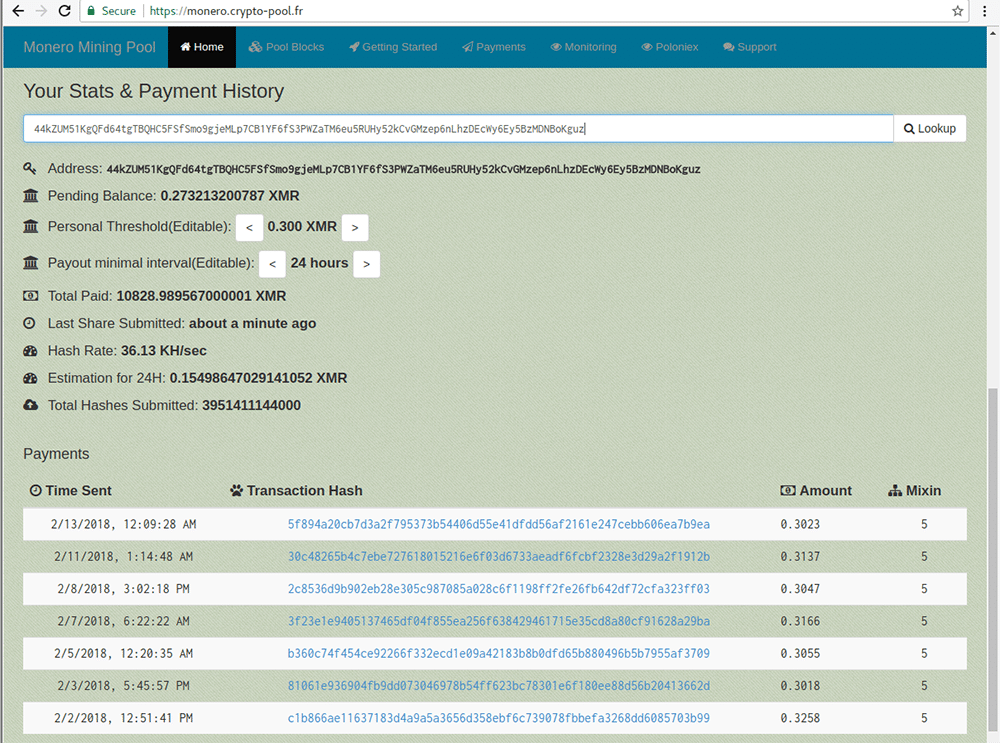
$3m Dollar Monero Waller. Source: checkpoint.com
Importance of Updates
The common thread in most of these exploits is that the vulnerabilities have been known. Much like the massive Wannacry attack last year with the Eternal blue exploits, the Jenkins vulnerability was known for some time.
When the vulnerability was made known by the developers, everyone should have updated their software immediately. However, out of convenience and lack of motivation, some developers left the vulnerability open.
If you want to make sure that your computing resources are not making someone else rich, update your software.
Featured Image via Fotolia
Disclaimer: These are the writer’s opinions and should not be considered investment advice. Readers should do their own research.
