In the vibrant and often tumultuous world of cryptocurrency, crypto hacks have become an unfortunate frequent occurrence, proving to be a difficult issue to overcome and casting a long shadow over the industry's revolutionary potential.
These breaches, often dramatic and costly, not only shake investor confidence but also spotlight the intricate balancing act between innovation, security, and regulation in the digital age. As breaches in DeFi have hit record levels, not only in frequency, but the sheer scale of funds stolen, not only is investor confidence shaken, but many feel that the future of trust in DeFi in its very essence could be at risk.
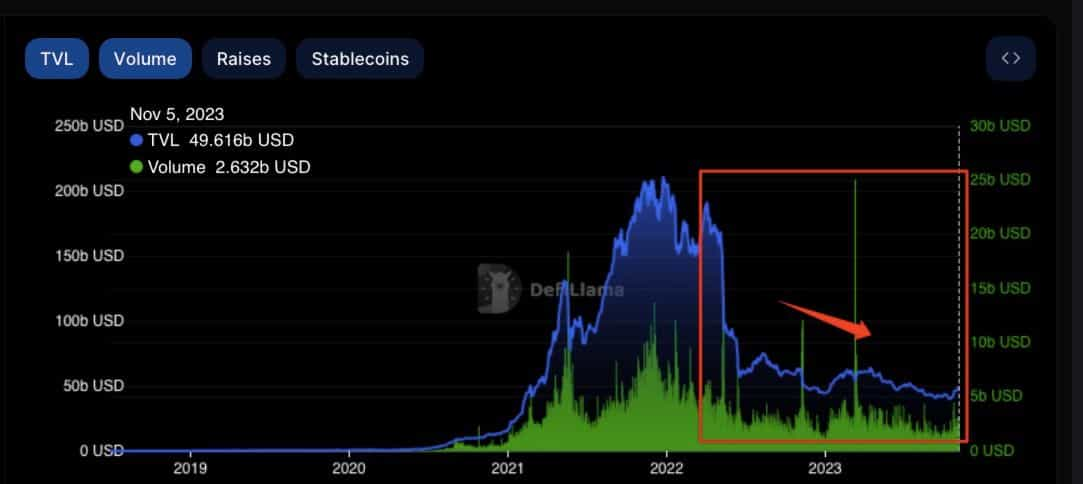
As someone with a TradFi background who has witnessed firsthand, the corruption and fragility of the traditional financial sector, I have long been inspired by the concept of decentralized finance and I’ve been a long-time user of DeFi DApps and protocols. But even for myself, the events of the past couple of years are causing my own DeFi convictions and confidence to waver, and record low levels of TVL and interest sentiment across DeFi protocols shows that I am not alone in my newfound skepticism and overly-cautious approach to decentralized finance. The industry has also appeared to reach a new level of lethargy to security breach headlines that seem to be making news headlines every week.
Hacks and security breaches used to be big deals, but now everyone seems to shrug and go “Oh well, just another day in crypto.”
In light of my concerns, which seem to be echoed across the broader crypto industry, I was thrilled for the opportunity to meet up with the team over at Hacken to field some of my questions and concerns and investigate why security breaches have become so commonplace, and ultimately, if there is any hope for a safer future for DeFi.
If you aren’t aware, Hacken is a team of cybersecurity and blockchain experts who specialize in auditing smart contract protocols and blockchain projects. They have become a true leader and trusted name in the industry, providing a much-needed service in helping protocols bolster their security to give them the best chances at fending off those fiends who seek to do crypto users harm.
If you need a primer on the subject and are unsure of what security auditors do, we cover that in our article on How to Understand Blockchain Audits to Stay Safe in DeFi.
Now, without further ado, let’s get into some background on crypto hacks, get Hacken’s expert opinions and insights as to why hacks appear to be getting worse, and if there is any hope for DeFi’s future.
What are Crypto Hacks?
Crypto security incidents come in many different forms, targeting individuals, companies, protocols, exchanges, smart contracts, or blockchains themselves. Nothing is off-limits; If it holds crypto, it may be the target of a hack attempt. These attackers are sometimes known, sometimes unknown, and the hackers can be individuals or entire organized groups committing these dastardly deeds and preying upon innocent crypto hodlers.
Examples of “lone wolf” hackers are the likes of the Poly Network hack in 2021, in which the anonymous hacker claimed the $600 million crypto heist was done “just for fun” and later returned the funds.
Then there are more sinister hackers such as The Lazarus Group, a known hacking syndicate from North Korea that is believed to be behind some of the largest crypto hacks in history.

Not-So-Fun Fact!- South Korean crypto exchange Upbit was reported to have been targeted by hackers more than 159,000 times in the first half of 2023, an increase of 117% from the previous year.
Long story short, crypto hacks refer to cyber attacks that exploit vulnerabilities that allow hackers to steal digital assets or manipulate the markets in their favour.
Crypto hacks and hack attempts are certainly gaining momentum, resulting in loss of trust and confidence in the industry.
The Silver Lining to Crypto Hacks
It’s not all doom and gloom, and while it would obviously be best to never have another security breach in crypto, there is a silver lining to take from them. These hacks, while unfortunate, serve as a wake-up call as they push the industry towards better security measures. Think of it as an evolutionary push, where every attack leads to stronger defenses. The industry is in a continuous race to outsmart these digital thieves, constantly upgrading and innovating to safeguard assets. It's a cat-and-mouse game, but one that’s crucial for the survival and thriving of cryptocurrencies.
Moreover, crypto hacks have a curious way of bringing people together. The community rallies, often working in unison to track down hackers or recover funds. This sense of solidarity, born out of crisis, is unique to the crypto world. It's an ecosystem that thrives on collaboration and open-source principles, where users stand generally in solidarity and are all concerned about everyone’s safety in the crypto community.
And let's not forget the regulators. They're often viewed as the bad guys in the crypto carnival, but they play a vital role. Each hack rings alarm bells, prompting governments and financial bodies to step up their game. Regulations tighten, oversight increases, and though it isn’t always for the best and there is always the risk of regulators overstepping their authoritative boundaries, it will most likely help mature the industry in the long run. A bit of discipline can be a good thing, ensuring that crypto doesn’t remain the Wild West of the financial world.
Common Crypto Hacks & Attacks
Crypto hacks can be executed through various methods, each exploiting different vulnerabilities. Here are the primary attack vectors:
1. Exchange Hacks- Targeting cryptocurrency exchanges to steal user funds. Hackers might exploit security weaknesses in the exchange's infrastructure, such as poor code, inadequate security protocols, or phishing attacks to gain access to users' accounts. Some of the largest exchange hacks include the likes of Binance, which was hacked for $40 million in 2019, FTX, which was hacked for $600 million in 2022, KuCoin, which was hacked for $280 million in 2021, and the list goes on. This is why we always preach the importance of self-custody and never leaving your crypto on an exchange!
2. Wallet Hacks- Attacking individual cryptocurrency wallets, especially those connected to the internet (hot wallets). Hackers use methods like keylogging, private key harvesting, MiTM attacks, phishing, or exploiting software vulnerabilities to access private keys. One notable example of a wallet hack was the Atomic Wallet hack in 2023, which resulted in over $35 million stolen.
3. Smart Contract Vulnerabilities- Exploiting flaws in smart contracts on blockchain platforms. Since smart contracts are self-executing contracts with the terms directly written into code, any coding error or oversight may be exploited. These are among the most common types of attacks, with a notable event being the Solana to Ethereum Wormhole Cross Chain Bridge attack that occurred in 2022, resulting in a loss of nearly $320 million.
The most common types of smart contract vulnerabilities are:
- Flash loan attacks
- Reentrancy Attacks
- Rug Pulls
- Access Control
I won’t go into detail on each one as Lossless has a great article covering The Most Common Smart Contract Vulnerabilities if you want to get into the technical details of common exploits.
4. 51% Attacks- Occur when a group of miners controls more than 50% of a network's mining power, allowing them to disrupt the network by double-spending coins or preventing new transactions from confirming. Ethereum Classic has fallen victim to multiple 51% attacks, resulting in prominent exchanges OKX threatening to delist Ethereum Classic due to a severe lack of security and Coinbase extending deposit and withdrawal confirmation times for ETC to roughly two weeks.
5. Phishing and Social Engineering- Using deceptive tactics to trick individuals into revealing sensitive information like private keys or wallet passwords. In 2023, a successful social engineering hack was carried out against an employee at CoinsPaid, resulting in the theft of $37 million. These can be quite complex and elaborate schemes. In the CoinsPaid case, it took the attackers six months to construct their plan and execute. Social engineering attacks are dangerous and even some old-school crypto-security-minded users have fallen victim to these intricate schemes.
6. Sybil Attacks- Creating a large number of pseudonymous identities to gain a disproportionately large influence on a network. Hacken does a great job in their article that covers the different types of Sybil Attacks and the threats they pose such as breaching privacy and hijacking blockchains.
7. Distributed Denial of Service (DDoS) Attacks- Overwhelming a network or service with a flood of network traffic to disrupt its normal operations. One of the most recent large-scale DDoS attacks was experienced by Solana in 2022. A group of hackers used a botnet to flood the Solanana network with traffic, bringing down the entire network for several hours.
8. API Exploits- Many exchanges and wallets use APIs for various functions. If these APIs are not properly secured, hackers can exploit them to access user accounts or redirect funds. This happened to Binance in 2019 when a hacker initiated a phishing attack to steal API keys and 2FA codes from users. They then used the credentials to place a large number of unauthorized trades on Binance, causing the price of Viacoin to skyrocket and then sold their holdings at the inflated price for a profit.
If you want to go further down the rabbit hole of different types of cybercrime, ransomware, malware and hacks, we go into greater detail in our article on Cybercrime and Security Concerns in Crypto.
Why are Crypto Hacks Increasing?
I was eagerly anticipating the Hacken team’s insights, and this was one of the first questions I had in mind. Hacks and exploits have only been getting worse, with 2022 and 2023 seeing record numbers for exploits.
I want to give a special thanks to Hacken’s Smart Contract Auditors:
For taking the time to provide us with their expert insights.
The team went on to explain that the severity of the hacks is a natural reflection of the growing size of the crypto industry. As more users enter the crypto markets, projects experience higher numbers reflecting Total-Value Locked (TVL), so naturally, exploits on the bigger and more widely used platforms will see greater losses.
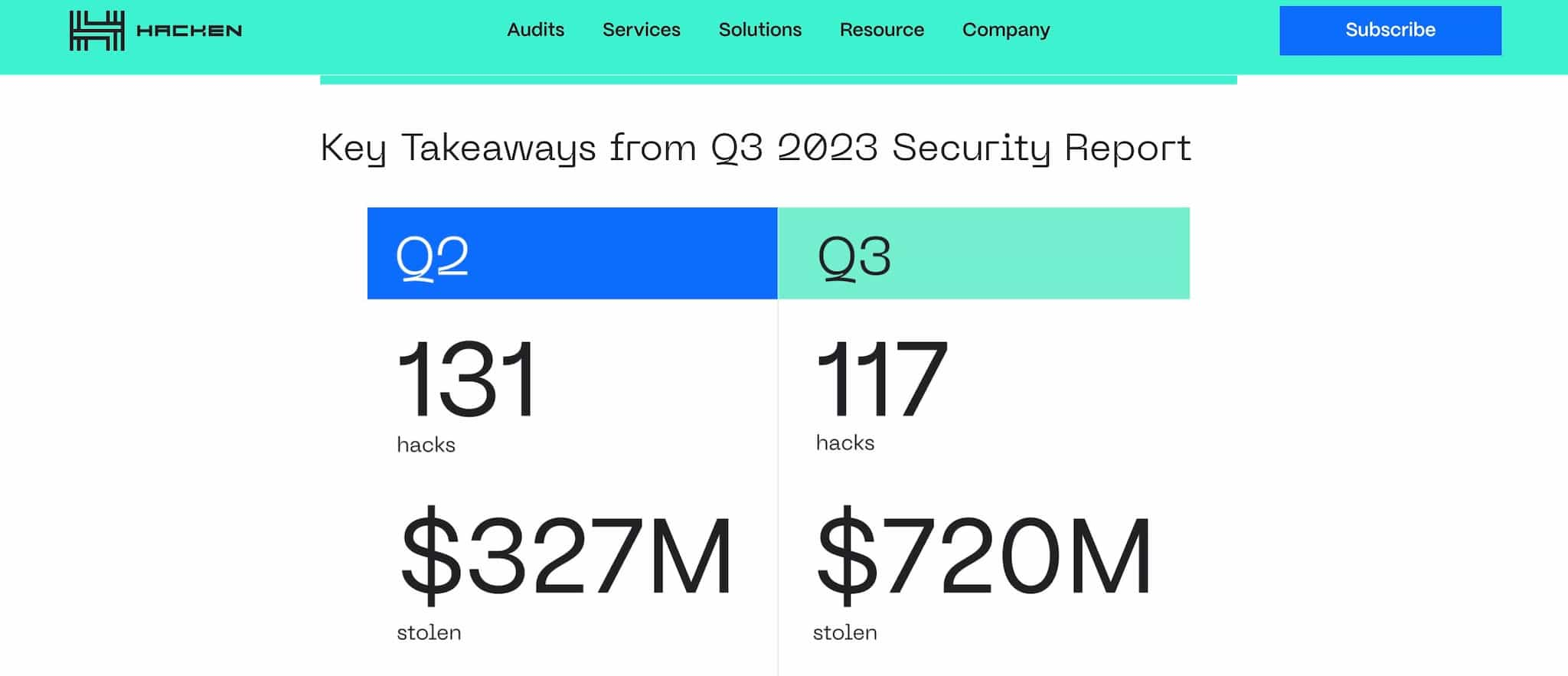
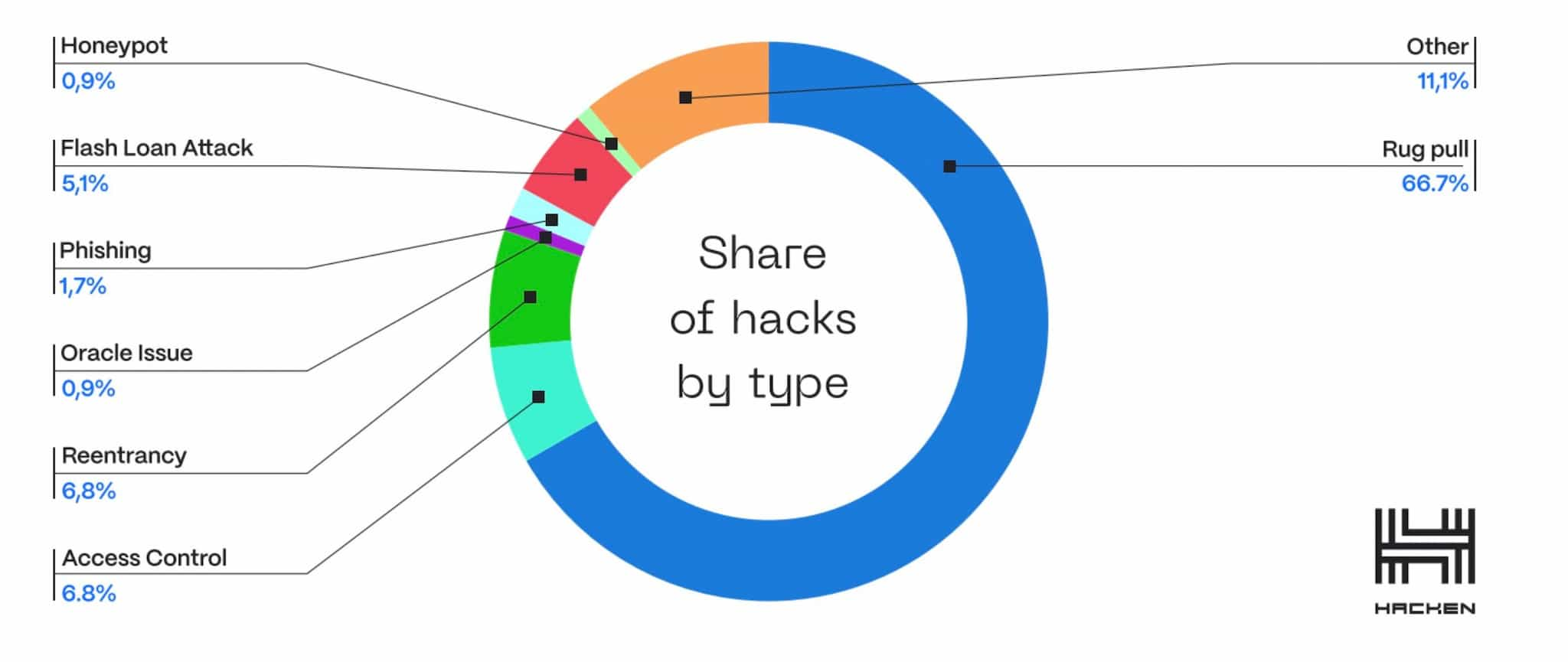
The image above was taken from Hacken’s Security Report, which went on to highlight the following key findings:
- Q3 saw 117 major security breaches: $720 million was stolen across 117 major breaches in just three months, highlighting the urgency of tighter security measures.
- Access Control is more important than ever: Access Control breaches remain the most devastating type of vulnerability in the crypto space.
- Rug pull frequency: Rug pull frequency is not diminishing and remains a popular tactic used by malicious actors who prey on investor greed, exploiting hype and FOMO.
- Lack of security audits: Of the 78 rug pulls examined, only 12 reported having undergone any kind of audit.
In Hacken's 2023 security report, they highlighted the following concerning points:
90% of crypto projects affected by security breaches did not have audits done and 85% didn't have a bug bounty program.
As for why the frequency has been increasing, Hacken went on to explain that a large reason is that projects feel rushed to hit the market and often do not undertake the proper audits and security measures. Proper security processes and procedures take time, and time is money in this game, so projects are eager to launch, taking shortcuts when it comes to security.
This is especially true in a bull market as everyone wants their project rolled out to catch the bull run euphoria, and as demand is highest for smart contract security auditors during these times, many projects choose to launch and not wait for a reputable auditor to become available.
Hacken recommends that there should be a framework for security that is similar to this:
- Minimize the impact of wrong security assumptions: e.g. Developers will often assume that the compiler they are using is not broken. We recently saw this incident play out with Curve, as a developer assumed that the compiler, which was only developed by 1 dev, was secure, and this was one of the major catalysts that led to the Curve hack.
- Understand what the project is about: Many projects don't have a complete idea of what functional requirements are needed to happen behind the scenes in order for a protocol to function. This makes it difficult to write accurate testing requirements.
- Test-driven development: Once the security assumptions are done and the functional requirements are chosen, it is time to write tests that check for security issues and requirements violations, only then is it time to write the actual code. Many projects jump straight in, writing code first without taking the appropriate security precautions beforehand.
- Audits with bad companies: There are companies that have a terrible ratio of audits performed/projects hacked, those companies should be avoided. Not every blockchain security audit company is created equal, and many projects aren’t willing to wait for top-rated security firms to become available to audit their project.
Pro Tip: When the team here at the Coin Bureau are doing our due diligence looking into who performed the audits for blockchain projects, the reputable names we look for are the likes of Hacken, Trail of Bits, Quantstamp, PeckShield, Certik, OpenZeppellin and Ackee Blockchain. That is not an exhaustive list, but some of the ones we trust.
The 4 points above outline a generalized and incomplete framework, but it provides a good starting point as some of these points are overlooked by the vast majority of protocols.
Here is a look at the comprehensive audits undertaken by leading DEX aggregator 1Inch:
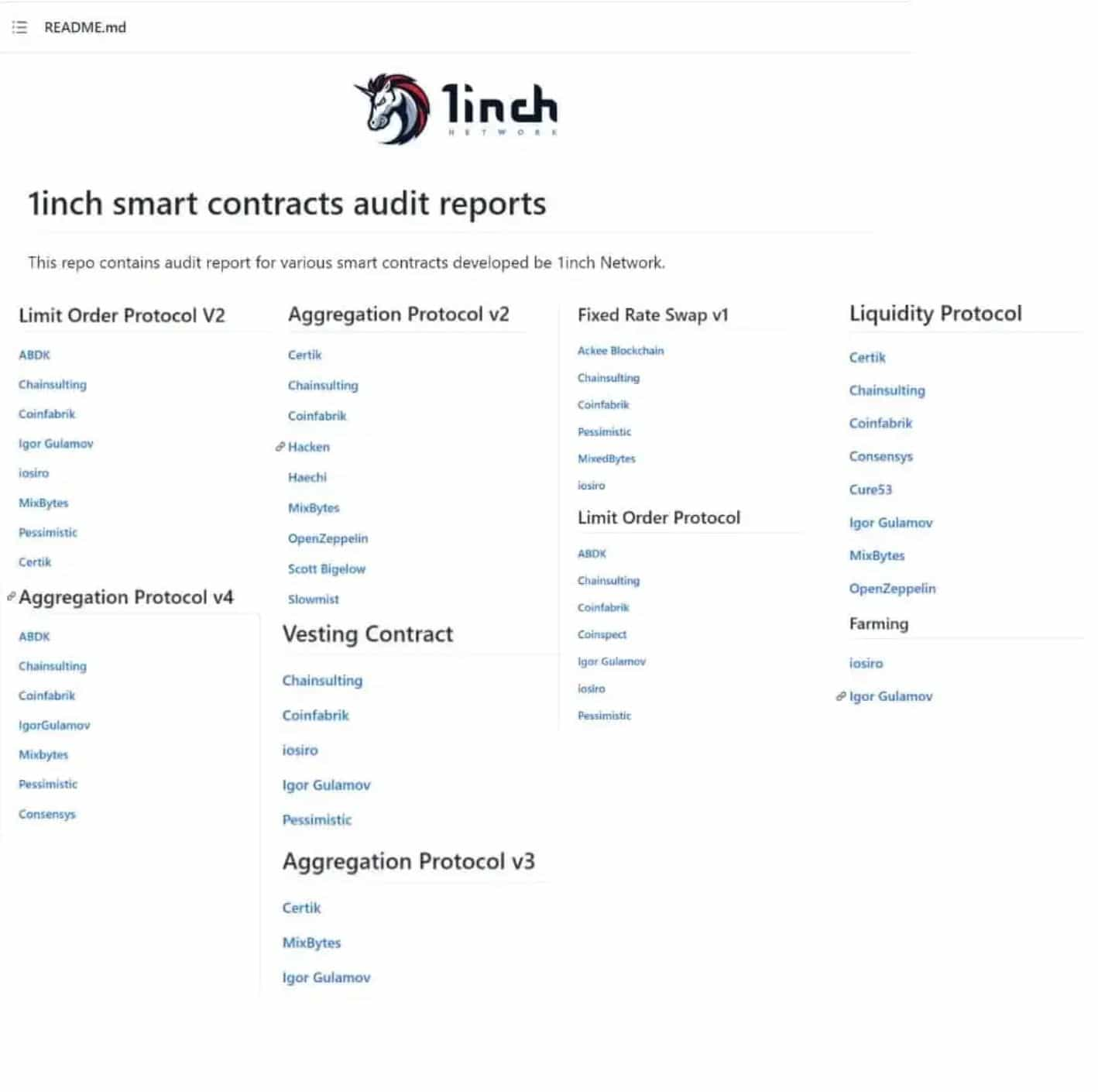
The 1Inch audits shown above are a great example of a platform that takes the security of their platform seriously, having each version of audited, separate protocols audited, and multiple security companies auditing the same code.
It is important to note that just because a company has had an audit done, there is never a 100% guarantee that a protocol is hack-proof.
One of the major issues seen is that less experienced project teams may not recognize the importance of having another audit done after they update or adjust a smart contract/protocol code. If a project undergoes an audit, then makes changes to the code over the coming weeks or months, the original audit is much less relevant, possibly even obsolete, depending on the complexity of the changes and another audit should be completed after each adjustment.
The Hacken team even go on to suggest that it is good security hygiene to have new audits performed after a period of time, even if there are no changes to the code as new vulnerabilities are discovered all the time such as a read-only reentrancy attack (see Curve’s oracles manipulation).
Crypto users can verify the results of crypto audits for themselves and even check a project’s Github page to see if there have been changes to a project’s code since the last audit. We cover the step-by-step guide on how users don’t need to trust, but can verify this information for themselves in our article on Blockchain audits.
Another trend seen by Hacken and ourselves here at the Bureau is projects hiring inexperienced coders to save on hiring costs. Like anything in life, you can’t expect to build lasting and high-performing products or services with an inexperienced and amateur team. The less experience a project team has, the higher the likelihood that there may be mistakes in the code and improper security protocols followed.

Inexperienced projects, or ones that rush to market may also try to cut down costs on the audit scope and might avoid further audits when the code is updated.
Emerging Technology is Uncharted Territory
Emerging technologies such as cross-chain bridges are very new and experimental, making them more susceptible to vulnerabilities. Many projects will release their smart contract protocols to the public and it essentially becomes trial by fire.
It isn't merely about coding securely, there are other problems that arise. It is not only the code but every single element that needs to be secure:
- The code
- The architecture
- Private key management
- Operational security (OPSEC) of the multisig controlling the bridge
Oftentimes there are weaknesses in one or more of the above. Almost every bridge hack has been a combination of small mistakes in these various fields.
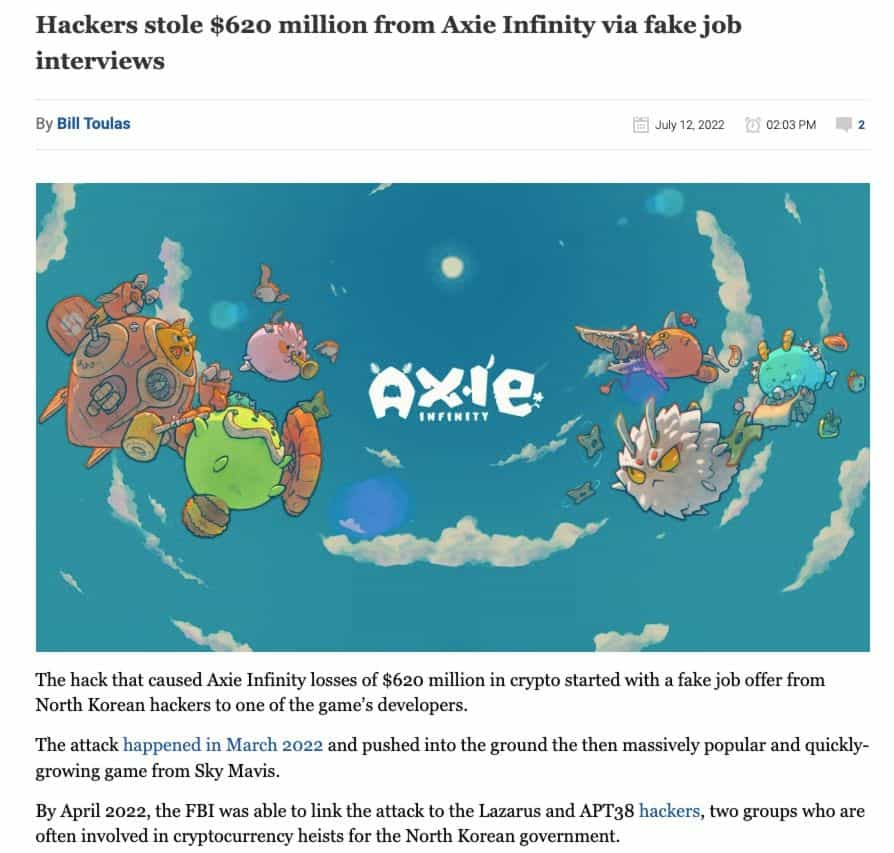
The Axie Infinity Ronin hack is among the most prominent examples to date. Hackers managed to get access to private keys to validator nodes resulting in the compromise of five nodes, which were needed to approve transactions. The root of the exploit was traced back to a year prior when Axie DAO gave access to Sky Mavis to approve transactions on its behalf to mitigate user volume. The crux of the mistake was that this access was never revoked, which led to backdoor access by hackers resulting in the $620 million loss.
Many inexperienced projects also fail to understand that there are different audits that should be conducted for different areas. For example:
- Smart contract - Projects should have a Smart Contract audit done. This step should be repeated for updates and changes to the smart contract code
- Infrastructure - dApp audit / Penetration testing should be conducted.
- Key management - CCSS audits should be performed.
The Complexity “Behind the Scenes”
DeFi protocols are often launched without the full scope of functionality understood. Some teams want to launch a project that can do "X" but do not understand all the steps needed to go from point A to Z in order to achieve “X”. This leads to communication issues when directing the team of coders as the developers follow the direction of the project founders who may not fully understand the entire process. This issue becomes especially prevalent if the developers are hired on a freelance basis.
Oftentimes, the founders of a DeFi protocol will have a vision and know what they want their platform to be able to achieve, but they may not have a technical background or won’t understand the technical steps needed for the series of complex steps that need to happen behind the scenes. As they hire freelance contractors to write the code, the coders simply follow the orders of the founders in a classic case of the blind leading the blind.
The Technological Race: Innovation vs. Security
The cryptocurrency world is in a constant state of flux, driven by rapid technological advancements. However, this innovation often outpaces the development of robust security measures. Despite testing protocols in sandbox and testing environments, the real test often comes once a project goes live and the protocol is flooded with network activity and injected with liquidity.
To quote Justin Drake, a researcher at the non-profit Ethereum Foundation about the merge to ETH 2.0
“The metaphor that I use is this idea of switching out an engine from a running car.” (Source)
The quote above highlights the complexity and potential dangers involved with developing blockchain technology in live environments, but testing environments are not always a possibility nor always an accurate reflection of the “rubber hitting the road” to keep with the car analogy.
Each new blockchain, bridge, smart contract, DeFi protocol, or DApp introduces new potential vulnerabilities, turning them into a hacker's playground. It's a classic tale of two steps forward, one step back – as the industry evolves, so must its security, often in reactive rather than proactive ways.
Then we also have to consider the immense amount of pressure coming from competition in the space. There is a crucial advantage often achieved by the first project to market in what is known appropriately as “first mover advantage.” This rush to market to beat the competition is also the cause of many shortcuts in the space.
Can We Do Better As An Industry and Minimize Exploits?
This was another area I was keen to hear Hacken’s expert insights about. In complete transparency, the events of the past two years have me hiding funds on my hardware wallet like a frightened turtle, only exposing a small percentage of my portfolio to DeFi, funds that I feel I can afford to lose.
I know many crypto hodlers have followed suit, which is a shame as there are billions worth of assets collecting proverbial digital dust in hardware wallets, never seeing the light of day as people are afraid of exposing their hard-earned digital assets to the risks of protocol exploits.
This is not the way it should be. The revolutionary potential of Decentralized Finance should be something that is available and freely enjoyed and accessible by everyone, without the constant worry that you could wake up one day to find the platform was hacked and your funds are gone.
This is the DeFi future we all want and need. As I have been genuinely wondering if I will ever be confident enough to expose more of my portfolio to DeFi protocols, it was great to hear the Hacken team have a more positive disposition than my worst-case worries and fears.
So, when I essentially asked, “Is there any hope for DeFi and DApps?” Here was their response:
- Blockchain technology is still a fairly early technology. As a new generation of skilled developers are trained and become more experienced, the code should have fewer vulnerabilities.
- Blockchain auditor companies like Hacken are growing, more auditors conducting more audits should reduce exploits.
- Project teams are learning about the importance of having regular audits done, and will likely learn that there should be an audit conducted after each update or change to code.
Let’s think about this question from the perspective of DeFi companies. In fact, it would be a good idea to create a lifecycle for projects from the very first step. As the teams allocate more budget for security, the protocol will be subject to more screening and security risks will gradually decrease at each stage.
That lifecycle could look something like this:
- Secure Development
- Unit & Fuzz tests with good coverage
- Smart Contract Audits
- Auditing Contests
- Secure Deployment
- Monitoring the project with 3rd party applications like Extractor
- HackenProof Bounty Program
Also, it is important to secure off-chain components. Penetration tests can be supportive to secure other components in protocols. The human factor should be also trained against phishing attacks (e.g. Buterin’s account takeover) through awareness training.
It was comforting to hear that there are plenty of steps projects can take to mitigate these concerns. Speaking to the true ethos and transparency of crypto, it is also good to point out that when a project undertakes an audit, good practice is to make the audit results publicly available. When researching DeFi platforms, we can often verify that there was an audit performed, we can see any security concerns that were highlighted, then a good audit company will also publish the steps the project took to address the findings.

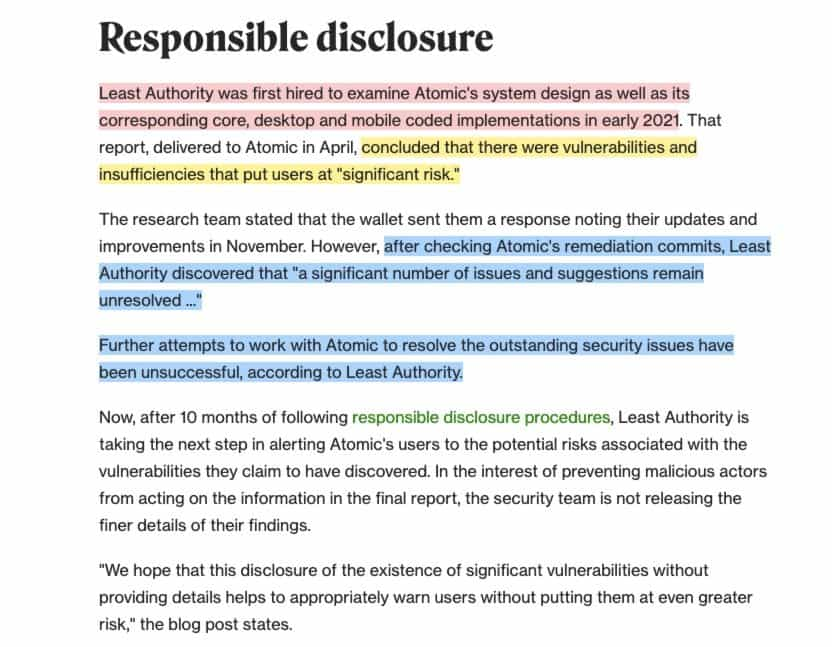
A good example of a project not addressing security concerns in an audit was the Atomic Wallet hack in 2023. After the hack occurred, members from the crypto community found a previous audit conducted which highlighted vulnerabilities that the Atomic Wallet team never addressed. If Atomic Wallet users had done more thorough due diligence, they would have found this publicly available information and may have chosen a different crypto wallet.
I wanted to change gears now and shift the focus away from project teams and audit companies and talk about everyone’s favourite topic: regulation in crypto.
As Regulation Is Introduced, Could This Enforce The Need For Properly Conducted Security Audits?
Hacken went on to explain that audits in Web3 lack any sort of standards and are de facto, only an informal code review by experts.
These security companies can also only highlight vulnerabilities and make suggestions, they cannot enforce action to be taken.
There are industry standards, such as EthTrustSpecifications by the EEA, but they are not legally binding. Hacken feels that security regulation is required and it could completely transform the Web3 environment for the better. This could lead to a legal framework to require security audits, their frequency, how they are done, etc.
I found myself agreeing with the Hacken team there, but it is important to point out that this sentiment is not shared among all users in crypto. Many in the industry like the “wild west” aspect of crypto and want no regulation or regulatory oversight at all. I can also sympathise with this point of view. Many in the industry I speak to who hold this opinion believe in the “survival of the fittest” concept where over time, the strongest projects will naturally emerge as the free market will determine which projects are worthy of longevity and user capital.
While I do agree that the free market approach would lead to this outcome over time, it would result in a lot more damage done to crypto users in the short term, turning away many “would-be” adopters for life and resulting in crypto’s prolonged reputation as being not a “serious asset class.” This would also likely slow the industry down by years, if not decades.
The pushback and fear about opening crypto to regulatory oversight chiefly resides in the likely outcome that the authorities will overstep, stifling innovation, and worst case scenario, destroying the ethos and libertarian values of crypto as it becomes just another corrupt and fragile arm of the traditional financial sector, the same financial sector that crypto was created for the need to replace.
It may be a naive pipedream, but many of us hope that a balance can be struck between safety and regulation while retaining an all-inclusive alternative financial system that cryptocurrency provides.

With breakthroughs in Artificial Intelligence far surpassing what many of us thought was possible in such a short period of time, I also wanted Hacken’s thoughts on AI and blockchain security.
Could AI Tools Help Auditors and Crypto Projects Find Vulnerabilities And Create More Secure Code?
Hacken feels that in the long run, it's likely that audits will increasingly lean on AI-powered assistants. AI can analyze vast amounts of code efficiently and spot patterns and vulnerabilities that might be overlooked by human auditors. Overall, it will enhance the efficiency and coverage of audits, making them more cost-effective and allowing for very frequent reviews, which is better for reducing Web3 hacks.
Best Practices for Preventing Crypto Hacks
For Companies
1. Implement Robust Security Protocols- Use advanced security solutions like end-to-end encryption, multi-signature wallets, and cold storage for the majority of funds.
2. Conduct Regular Security Audits and Penetration Testing- Regularly audit your systems and conduct penetration testing to identify and fix vulnerabilities.
3. Employee Training and Awareness- Train employees on security best practices, phishing recognition, and safe handling of sensitive information.
4. Use Secure Communication Channels- Ensure that all internal and external communications are conducted over secure, encrypted channels.
5. Monitor Transactions Continuously- Implement systems to monitor transactions in real-time for any suspicious activity.
6. Incident Response Plan- Have a well-defined incident response plan in place to quickly address and mitigate the impact of any security breaches.
7. Collaborate with Security Experts- Work with cybersecurity experts to stay updated on the latest threats and security measures.
8. Regulatory Compliance- Ensure compliance with relevant regulations and standards to enhance trust and security.
9. Bug Bounty Programs- Encourage ethical hackers to find and report vulnerabilities through bug bounty programs.
10. Limit Access- Implement strict access controls to sensitive systems and data. Only authorized personnel should have access to critical infrastructure.
For Individuals
Preventing crypto hacks is crucial for protecting your digital assets. Here are some best practices for individuals to help safeguard their cryptocurrencies:
1. Use a Hardware Wallet: Consider using a hardware wallet, such as an NGRAVE or Trezor to store your cryptocurrencies offline. Hardware wallets are less vulnerable to online attacks and provide an extra layer of security. Check out our picks for the Most Secure Hardware Wallets.
2. Enable Two-Factor Authentication (2FA): Enable 2FA anywhere that supports it. This adds an extra layer of security by requiring a second form of authentication, typically something you have (like a mobile app or hardware token) in addition to something you know (your password).
3. Choose Strong and Unique Passwords: Use strong, unique passwords for your exchange and wallet accounts. Avoid using easily guessable passwords and consider using a password manager to generate and store complex passwords.
4. Be Cautious of Phishing Scams: Be vigilant for phishing attempts. Hackers often use fake websites and emails that appear legitimate to steal login credentials. Double-check URLs, email senders, and only use official websites and links.
5. Keep Software and Firmware Updated: Regularly update your wallet software and firmware. Developers release updates to patch security vulnerabilities and improve the software's security features.
6. Educate Yourself: Stay informed about the latest security threats and best practices. Understanding common attack methods, like social engineering and malware, will help you avoid falling victim to them. You can learn more in our articles on Cybersecurity and our Crypto Safety Guide.
8. Beware of Public Wi-Fi: Avoid using public Wi-Fi networks when accessing your cryptocurrency accounts or making transactions. Public networks can be less secure, making it easier for attackers to intercept data.
9. Secure Your Devices: Ensure that your devices, including your computer and mobile phone, are secure. Use up-to-date antivirus software, enable firewalls, and keep your operating system and software updated. We also recommend using a good VPN to encrypt your online communications.
10. Diversify Your Holdings: Diversify your cryptocurrency holdings to reduce risk. Don't put all your assets in a single wallet or exchange. Spreading your investments can help minimize potential losses in case of a security breach.
11. Use Multisignature Wallets: Multisignature wallets require multiple private keys to authorize transactions. They can be an extra layer of security since multiple parties must approve transactions.
12. Backup Your Wallet: Regularly back up your wallet's data and store backups in a secure location. It is also a good idea to access your hardware wallets periodically to ensure you remind yourself of any passwords, pins, or passphrases you may have used with the wallet.
13. Enable Withdrawal Whitelists: Some exchanges and wallets allow you to set up withdrawal whitelists, which only permit withdrawals to specified addresses. This can prevent unauthorized transfers.
14. Be Cautious of Social Engineering: Be wary of unsolicited communication or requests for personal information, even if they seem to come from legitimate sources. Verify the identity of anyone asking for sensitive information. A good rule of thumb is that anytime there is a link to a company you trust in an email asking to update or verify information, you can navigate to your account on their platform using the URL as you normally would and double-check the communication there. You can also use tools like the Norton URL checker or URLVoid to help identify dodgy phishing sites.
15. Consider Insurance: Some insurance companies offer crypto insurance to protect against theft and hacking.
Now, onto the big question.
What Does the Future Hold?
Are we doomed to an endless cycle of crypto hacks?
Though the past two years have been especially painful for crypto users, as the old cliche goes, it’s always darkest just before the dawn, and I am hoping the dawn will be an enlightening awakening for the crypto community, a call to arms if you will, where projects learn from the atrocities of 2022/2023 and start placing a stronger emphasis on security over profit and rushing to market.
I found Hacken’s take reassuring. The industry is learning, albeit through a trial by fire. Each hack is a lesson, a harsh reminder of the need for tighter security protocols, better user education, and perhaps more regulatory oversight.
However, I do want to caution users who may be getting into crypto for the first time before experiencing their first euphoric cycle of a bull market. I am going to go ahead and assume that come the next bull market, we are going to see the same mad rush to market from project teams who are going to throw caution to the wind and want to simply get their protocol running to capitalize on the flow of capital that enters the market during bull market stages. It’s human nature and something that isn’t likely to change.
But over time, as crypto bear and euphoric bull markets become less extreme and crypto’s ebbs and flows become more stable over time, I believe that the industry will mature and that there will be less scrambling from projects trying to launch and ultimately, the frequency and severity of breaches will be minimized.
But, as we wait for that to happen, if this article and our piece on How to Understand Blockchain Audits helps even just a handful of people to avoid losing their funds in a security exploit, then here at the Bureau, we consider that mission success.
A big thanks again to the Hacken team for lending us their opinions and insights. In this digital age of information, knowledge and education are a valuable resource.
Frequently Asked Questions
The most common types of cryptocurrency hacks include phishing attacks, malware and keyloggers, exchange breaches, SIM-swapping, and various scams and Ponzi schemes. Users can protect themselves by practicing good security habits, using hardware wallets, enabling two-factor authentication, and staying vigilant against fraudulent schemes and phishing attempts.
Recovering stolen cryptocurrency is challenging due to the semi-anonymous nature of blockchain transactions, but in some cases, with prompt action and cooperation from exchanges, it can be possible. Though most smaller-sized crypto thefts go unrecovered.
While hardware wallets are among the most secure options, no system is entirely foolproof. It's crucial to follow best practices even when using hardware wallets.
Look for platforms that have robust security measures, such as multi-factor authentication, regular security audits, and a strong track record of security. We like to use free tools such as De.Fi which is the largest database for smart contracts audits. Users can paste a smart contract address, look up DeFi protocols and more in De.Fi and get security insights.
Disclaimer: These are the writer’s opinions and should not be considered investment advice. Readers should do their own research.


