Verge (XVG) Suffers a Severe Miner Network Attack
Verge (XVG), the privacy-conscious cryptocurrency, suffered a dreaded 51% network attack today.
This was according to a highly respected miner and the administrator of the Suprnova mining pool. The discovery was laid out in a BitcoinTalk forum post where he detailed that the malicious miner was able to exploit bugs in the retargeting of XVG code.
This allowed the miner to mine a XVG block once every second within a three-hour time period earlier this morning. The moment that the poster (OCMiner) mentioned the attack, the malicious miner stopped his pool.
So what exactly is going on with Verge?
Timestamp Spoofing
Verge mining is a bit unique in that each Verge block is mined according to a different algorithm. So for example one block will be mined with Scrypt and the other with blake etc.
The Verge protocol will check the previous block to confirm what algorithm was used. However, given a bug in the Verge code the miner is able to submit blocks with false timestamps. Hence, the miner is able to trick the algorithm into thinking that the last block that was mined was over an hour ago.
According to OCMiner:
Your next block, the subsequent block, will then have the correct time... And since it's already an hour ago (at least that is what the network thinks) it will allow this block to be added to the main chain as well
He then posted a breakdown of all of the blocks that the miner was able to submit. They all followed each other but had different time stamps. The block with the spoofed time stamp was immediately before a correctly timed block. The result of this exploit was that the hacker was able to mine a block once every second.
There were also other miners who mentioned problems they were having mining during that particular window. OCminer also linked to a number of the addresses that were used in order to offload the mined coins. There were no doubt many more.
Response from Verge
When this was brought to the attention of the Verge developers, they first claimed that there was nothing to correct. However, after the clear demonstration of the attack they pushed a "fix" and issued a tweet.
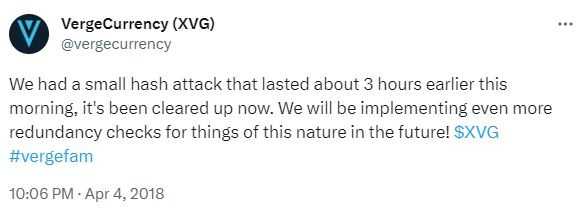
Of course, there were many in the Verge community who did not take kindly to the post on Bitcointalk. They replied to the original post with the usual prognostications of "FUD" and someone trying to "pick up" cheap Verge coins.
This is indeed unfortunate as the pool operator was in fact helping the community out. By spotting the network attack early and bringing coverage to it he managed to get the attacker to think twice. Moreover, it gave helpful information to the Verge Devs in order to correct the exploit.
More Trouble for Verge?
This comes at a time when opinion about Verge is highly split. There are die hard adherents of the "vergefam" phenomenon who think that it could legitimately be the next big privacy conscious cryptocurrency.
However, there are many others who view the tactics recently employed by Verge as dubious at best. For example, just last week the Verge team sent out a fundraising request in order to raise more money for securing a "secret deal".
In the end, they managed to raise the required funds and have now moved the announcement date to the 17th of April. This has created a great deal of speculation and indeed confusion from both sides of the divide.
As the miner attack shows, there are still some technological challenges for Verge to overcome if they truly want to take on more established cryptocurrencies. One can only hope that no further exploits are discovered.
Updated 22 May
It may shock no one to learn that the Verge attacker was able to find a way around the minor patch that was implemented by the Devs. And they have used this to mint millions more XVG.
OC miner, the same person who spotted the original vulnerability, brought it to the attention of users on Bitcointalk.
In this case, the attackers merely used two algorithms instead of one. He then was able to fork the chain by renting hashing power for these two algorithms.
The hacker is still using the same timestamp spoofing that would impact the difficulty adjustments on the network. Expect this time he is not only using scrypt but also lyra2re.
At the time of writing, the malicious miner was able to mine blocks 2155850 to 2206272 which is about 35m XVG. This is equivalent to about $1.7m that the hacker was able to earn again.
What did the devs do about it?
They merely labelled it an "ongoing DDOS" attack with not that much more explanation. However, they have used the opportunity to explain that they will be rolling out a completely updated codebase.

Although something appears to be done, many will say that it is too little too late. Although Verge has done a great deal in the way of marketing with partnerships such as PornHub, the fundamental flaws remain.
If the developers are able to release a completely new codebase and they use a rigorous peer review, it is possible that they could recover.
However, as many would say: Fool me once, shame on me, fool me twice, shame on you...
Featured Image via Fotolia
Disclaimer: These are the writer’s opinions and should not be considered investment advice. Readers should do their own research.
