As the world strides into the digital future, we stand on the threshold of a new era in internet technology: the advent of Web3. This evolution marks a significant departure from its predecessor, Web2, and heralds a transformative era characterized by decentralization, enhanced data ownership, and unparalleled privacy. Unlike the incremental updates that defined the progression of the internet in the past, Web3 represents a fundamental shift, offering a vision of the internet that empowers users with unprecedented control over their online data.
Web3: A Revolution in User Empowerment and Control
Web3 is set to redefine the user experience on the internet. At its core, it is about shifting the power dynamics of the digital world, placing the control firmly in the hands of the users. This new paradigm allows individuals to dictate how, where, and with whom their data is shared across the internet. This empowerment is not just a feature of Web3; it is its cornerstone, rooted in principles of decentralization, permissionless interaction, and rigorous privacy. The goal is clear: to achieve Web2 equivalence where Web3 platforms can perform all the functions and capabilities of the current internet while upholding these newfound principles.
The Transition from Web2 to Web3
The journey from Web2 to Web3 marks a significant shift in how we treat data. In the Web2 era, centralized platforms held sway, controlling user data and often monetizing it without the users' explicit consent. Web3 challenges this status quo by decentralizing data control, ensuring that users retain ownership and have a say in capitalizing their data. This approach not only enhances privacy but also paves the way for innovative applications that were previously unimaginable under the centralized models of Web2.
To better understand the impact of and significant of Web3, we explore this topic in detail in our article: Evolution of the Internet: How Web3 is Changing our Digital Lives.
HTTPS and VPNs: The Protectors of Privacy in the Traditional Internet
HTTPS has been the standard bearer for data security in the traditional internet landscape. It secures the connection between a visitor and the website, protecting the data transmitted in their interaction. HTTPS also plays a crucial role in ensuring that users connect to the legitimate version of a website, safeguarding them against various forms of cyber fraud. However, VPNs have become indispensable tools for those seeking an added layer of privacy. While HTTPS encrypts the connection to the website, a good VPN protects privacy by concealing user actions and interactions, thus preventing external entities like ISPs (Internet Service Providers) from monitoring Internet usage.
Blockchain Technology: The Vanguard of Web3
At the heart of Web3's vision lies blockchain technology. This piece will delve into the progress made by blockchain in mirroring the functionalities of Web2 while embedding the core principles of Web3. We will navigate the evolution of privacy technologies, dissect the regulatory frameworks surrounding private networks, and analyze the industry's trajectory in achieving internet equivalence. Our exploration will shed light on the milestones, challenges, and breakthroughs shaping the internet's future, paving the way for an era where privacy and ownership are not just ideals but tangible realities.
The Timeline of Blockchain Privacy Innovations
The journey of privacy in the cryptocurrency space reflects a constant balancing act between the need for privacy and the inherent transparency of blockchain technology. Each project has contributed new ideas and solutions, pushing the boundaries of what is possible in terms of transactional privacy and user anonymity.
1. Bitcoin and the Emergence of Cryptocurrency (2009)
Bitcoin's introduction in 2009 was a watershed moment in digital currency as it brought the concept of pseudonymity to the forefront. Transactions on the Bitcoin network are recorded on a public ledger, offering transparency while keeping the parties' identities obscured. However, this pseudonymity is limited; investigators can analyze transaction patterns, potentially exposing user identities. This inherent limitation in Bitcoin's design sparked a significant interest in enhancing privacy in the cryptocurrency space.
2. Darkcoin/Dash: Pioneering Enhanced Privacy (2014)
Originally named Darkcoin, Dash represented a significant step forward in cryptocurrency privacy. It introduced features like PrivateSend, which added an extra layer of privacy by mixing transactions, thus obscuring their origins. This feature made it significantly more difficult for outside observers to trace individual transactions to their source. Dash's approach to privacy was one of the first of its kind, addressing some of the limitations of Bitcoin's pseudonymity and setting the stage for future privacy-focused cryptocurrencies.
3. Monero: The Privacy Standard Bearer (2014)
Launched in the same year as Dash, Monero took privacy even further. It uses ring signatures and stealth addresses, which work together to obfuscate the origins, amounts, and destinations of transactions. Ring Signatures made Monero transactions virtually untraceable, cementing its position as one of the leading privacy coins. Monero's strong focus on privacy has made it a favourite among users who prioritize anonymity. Still, it has also been a point of contention due to its potential misuse for illicit activities.
4. Zcash: Introducing zk-SNARKs (2016)
Zcash marked a significant technological advancement in cryptocurrency privacy by introducing ZK-SNARKs (Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge). This technology allows transactions to be validated without revealing any information about them, offering users the choice between transparent and shielded transactions. Zcash's innovation has had a lasting impact on the crypto space, influencing many subsequent projects seeking to balance privacy with transparency.
5. Verge: Privacy Through Anonymity Networks (2016)
Verge focused on enhancing user privacy by obscuring IP addresses and using technologies like Tor and I2P. By integrating these anonymity networks, Verge added an additional layer of privacy to cryptocurrency transactions, making it more challenging to trace them back to the users involved. This approach to privacy addresses a different aspect than transactional anonymity, focusing on the users themselves and their interaction with the network.
6. Beam and Grin: Implementing Mimblewimble (2019)
Both Beam and Grin are built on the Mimblewimble protocol, which offers enhanced privacy and scalability. Mimblewimble's main feature is its ability to combine multiple transactions into one, reducing the blockchain's size and increasing privacy. Beam focuses on usability and compliance, while Grin takes a more minimalistic and community-driven approach. Despite their innovative technology, both Beam and Grin have faced challenges in gaining widespread adoption compared to more established privacy coins like Monero or Zcash. Litecoin also adopted the Mimblewimble protocol to enable privacy-enhancing transactional capabilities.
7. Secret Network: Privacy for Smart Contracts (2020)
Launched in 2020, Secret Network introduced a novel concept: privacy-preserving smart contracts. This platform allows developers to create decentralized applications (DApps) using encrypted data without revealing it on the blockchain. This innovation expands the scope of blockchain privacy from transactions to complex applications, opening up new possibilities for privacy in the decentralized finance (DeFi) sector and beyond.
Controversies and Regulatory Consequences of Evolving Blockchain Privacy
Significant controversies and an evolving regulatory landscape have marked the evolution of privacy networks and coins in the blockchain space. This development reflects the tension between the desire for privacy in financial transactions and concerns about the potential misuse of this technology. Let's explore some key controversies and how they have shaped regulations.
Bitcoin and the Silk Road Controversy (2011-2013)
While not a privacy coin, Bitcoin played a central role in the early controversies surrounding cryptocurrency privacy. Its use on the Silk Road, an online black market, highlighted the potential for digital currencies in fostering illegal activities. The Silk Road facilitated various unlawful transactions, using Bitcoin as the medium of exchange. This controversy drew significant attention from law enforcement and regulators, leading to the shutdown of the Silk Road in 2013 and the arrest of its founder, Ross Ulbricht.
Regulatory Impact: The Silk Road case was a wake-up call for regulators worldwide, highlighting the need for oversight in digital currency transactions. It spurred discussions about applying traditional financial regulations, like Know Your Customer (KYC) and Anti-Money Laundering (AML) laws, to the emerging world of cryptocurrencies.
Monero and Zcash: Enhancing Privacy and Drawing Scrutiny
Monero and Zcash, launched in 2014 and 2016, respectively, introduced advanced privacy features that addressed the pseudonymity limitations of Bitcoin. Monero anonymizes transactions using ring signatures and stealth addresses, while Zcash offers ZK-SNARKs for optional transaction privacy.
Controversies and Challenges: Monero and Zcash faced scrutiny due to their enhanced privacy features. Due to its strong privacy protections, Monero, in particular, became associated with illicit activities, including ransomware attacks. Although Zcash offers the option of transparent transactions, it also faced concerns over its potential misuse.
Regulatory Evolution: The enhanced privacy features of these coins led to a stricter regulatory response. Several countries and exchanges began delisting privacy-focused coins to comply with AML and KYC regulations. Japan, for example, saw its Financial Services Agency (FSA) pushing to delist privacy coins from exchanges in 2018.
The FATF Travel Rule and Its Implications (2019-Present)
The Financial Action Task Force (FATF), an international body setting standards for combating money laundering and terrorist financing, introduced the "Travel Rule" in 2019. This rule requires virtual asset service providers (VASPs) to collect and transfer customer information during transactions, including those involving cryptocurrencies.
Impact on Privacy Coins: The Travel Rule presented a significant challenge for privacy coins, as their inherent features often prevent the transparent collection and transfer of personal data, leading to increased pressure on exchanges and wallet providers to either find ways to comply or delist these coins.
The Tornado Cash Incident (2022)
Tornado Cash, a decentralized Ethereum mixing service, became a focal point of controversy in 2022. It was designed to enhance transaction privacy by obfuscating the origins and destinations of Ether transactions.
Controversy and Regulatory Action: Tornado Cash was implicated in laundering stolen funds, notably in the aftermath of the North Korean-affiliated Lazarus Group's hack of the Ronin Network. This led to the U.S. Treasury Department sanctioning Tornado Cash, a move that sparked a debate about privacy, decentralization, and the scope of regulatory actions.
Community Reaction and Legal Debates: The crypto community reacted strongly to the sanctions, with debates centring on the implications for software development and the rights to financial privacy. Legal experts also questioned the precedent of sanctioning a decentralized protocol rather than specific individuals.
Conclusion: Balancing Privacy and Regulation
The journey of privacy networks and coins highlights a complex interplay between innovation in financial privacy and the need for regulatory oversight to prevent illicit activities. As technology continues to evolve, so does the regulatory landscape, with governments and international bodies striving to adapt their frameworks to address the unique challenges posed by these technologies.
Blockchain Privacy is Not Absolute, But a Spectrum
The evolution of privacy within blockchain technology reflects a significant shift from its early conceptions to a more nuanced understanding today. Initially, privacy in blockchain was often perceived as an absolute concept — either a transaction was private or it wasn't. This binary perspective mirrors regulatory approaches, which frequently struggle to balance the need for oversight with respect for individual privacy. However, as blockchain technology has matured, so has our understanding of privacy, leading to the recognition of privacy as a spectrum of varying degrees and types.
Early Days of Blockchain and Privacy
In the early days of blockchain, the focus was primarily on the transparency and immutability of data. Bitcoin, for instance, introduced the notion of pseudonymity. While transactions are publicly recorded on the blockchain, the identities of the individuals behind these transactions are not directly visible. This form of privacy focuses on obfuscating the link between public addresses and real-world identities. However, advancements in blockchain analytics have shown that pseudonymity can be compromised, mainly when transaction patterns are analyzed extensively.
Shifting Perception of Privacy
This realization led to a shift in how privacy is perceived in the blockchain community. It is no longer seen as a binary state; it’s now understood as a spectrum. This spectrum ranges from completely transparent systems, like many government-led blockchain projects, to highly private networks like Monero and Zcash.
The Emergence of Functional Privacy
Beyond identity concealment, the concept of functional privacy has gained prominence. Functional privacy is not just about hiding who is transacting but also what they are transacting. It’s about obscuring the nature of the activity itself, which can include the smart contracts interacted with or the DApps used.
Understanding Functional Privacy: The Secret Letter Analogy
Imagine sending a letter in a sealed envelope. The postal service (akin to the blockchain network) ensures the letter gets from you (the sender) to the recipient. While the postal service knows who is sending and receiving the letter (the public addresses in a blockchain transaction), they cannot see what's inside the envelope (the contents of your transaction). This is similar to data privacy in blockchain: the transaction details (such as the amount transferred) are encrypted and kept private.
Examples in Blockchain:
- Bitcoin: Provides a basic level of data privacy through pseudonymity; the transaction amounts and addresses are visible, but the real-world identity of the address owner is not necessarily known.
- Zcash: Offers an advanced form of data privacy using zk-SNARKs, allowing users to hide the transaction amount and the parties involved.
Functional Privacy in Blockchain: The Exclusive Club Analogy
Consider an exclusive club where activities inside are not visible to those outside. Members (users) can enter the club (perform transactions or interact with smart contracts) and engage in various activities (different functions of the DApps or contracts), but outsiders can't see what any specific member is doing inside. This setup is akin to functional privacy in blockchain, where the functions or operations a user performs are hidden from public view.
Examples in Blockchain:
- Monero: Uses ring signatures to hide the sender's identity in a transaction, thus providing functional privacy regarding whom you transact with.
- Secret Network: This blockchain takes functional privacy further by enabling smart contracts to operate in a way where the data used in the contract and the nature of the interactions are kept private.
Ethereum and Bitcoin's Limitations
Both Ethereum and Bitcoin were not originally designed with functional privacy as a core feature. Their architecture and consensus mechanisms require certain transaction details to be visible for the network to validate and confirm transactions. For instance:
- Ethereum: Its consensus protocol requires visibility into addresses and signatures to validate transactions and construct blocks. This transparency is key to the network's functionality but limits the degree of functional privacy that can be achieved.
- Bitcoin: Similar to Ethereum, Bitcoin's design ensures transparency in transactions, essential for the network's integrity and trust model. This transparency inherently limits functional privacy.
In summary, data privacy in blockchain is about keeping the transaction details confidential, like a sealed letter. In contrast, functional privacy is about concealing the actions or interactions of the users, similar to activities happening in an exclusive club. Both forms of privacy are crucial for different use cases in blockchain, offering users a spectrum of privacy options depending on their needs.
Ethical Importance of Privacy
The ethical importance of privacy in blockchain cannot be overstated. Privacy is a fundamental human right; in the digital realm, it is critical to protect individuals from surveillance and data exploitation. The current regulatory mindset often views privacy through a narrow lens, primarily focusing on preventing illicit activities. While this is important, it sometimes overlooks the legitimate need for privacy in everyday activities. A more balanced approach is needed, one that recognizes the value of privacy in fostering innovation, protecting individual rights, and building trust in digital systems.
The Narrowed Mindset of Regulation
Regulatory bodies have historically had a challenging relationship with privacy in blockchain. Regulations often lag behind technological advancements, leading to a reactive rather than proactive approach. The focus has predominantly been on preventing money laundering and terrorist financing, sometimes at the expense of individual privacy rights. However, as the understanding of blockchain privacy deepens, regulators have an opportunity to develop more nuanced frameworks that protect both personal privacy and the integrity of financial systems.
Summary
The evolving concept of privacy in blockchain reflects a deeper understanding of the complexities involved in digital interactions. Recognizing privacy as a spectrum allows for a more flexible and nuanced approach to both technology development and regulatory frameworks. As the blockchain space continues to evolve, it’s imperative to balance the need for privacy with other considerations like security, regulatory compliance, and ethical responsibility. The future of blockchain privacy lies in finding this balance, ensuring that technology serves both individual rights and the broader societal good.
The Narrative Behind Privacy
This section looks at privacy from a new angle. It explores how the notion of privacy evolved to address its growing needs as the internet runs on a distributed ledger. Distributed networks represent a paradigm shift in digital networking such that existing notions of privacy no longer apply.
Pseudonymity is a Myth
Blockchain forensics focuses on connecting blockchain addresses to real-world identities. It involves analyzing metadata, correlating addresses with known identities, and leveraging external data sources such as available KYC information, IP addresses, or social media profiles to establish connections between on-chain and off-chain identities.
Investigators use chain analysis techniques like backtracking transactions and have access to tools like clustering algorithms. Blockchain surveillance systems also sniff out IP addresses connected to specific transactions, letting investigators estimate the geographical origin of Bitcoin transactions. When used in conjunction, these technologies seriously dent the Bitcoin Networks’ pseudonymity, forcing users to adopt more aggressive privacy measures.
Privacy vs Oversight
The dichotomy between privacy and oversight is a critical issue. Privacy in blockchain, epitomized by networks like Monero, offers robust protection of transaction details, ensuring users' financial activities are shielded from public view. This level of privacy is lauded for safeguarding individual rights and providing security against fraud and theft. However, it presents a significant challenge for regulatory oversight. Authorities, tasked with preventing and investigating illicit activities such as money laundering, terrorist financing, and tax evasion find tracing transactions on privacy-focused blockchains difficult. Consequently, regulators often view these networks with suspicion and may impose strict regulations or outright bans.
The challenge lies in developing technologies and regulatory frameworks that balance the need for individual privacy with the imperative of legal and financial oversight, ensuring that blockchain technology is used responsibly and ethically while also respecting the fundamental right to privacy.
Growing Demand for Functional Privacy
Blockchain privacy has legitimate use cases. The public nature of blockchain grants access to all transactions, public addresses, and balances. Individuals have devised elaborate methods to exploit this information in a variety of ways. There is an ethical need for functional privacy, which can enable some critical use cases:
- Resistance to MEV (Miner Extractable Value): By hiding transaction details, functional privacy can prevent front-running and other exploitative practices common in DeFi platforms.
- Importance in Digital ID Systems: Functional privacy can allow for verification without exposing sensitive personal information in systems where identity is crucial.
- Dark Pools: High net-worth individuals and institutions often utilize dark pools to trade large assets without revealing trade details. Dark pools are prone to front-running attacks.
- Data Privacy: Establishing systems ensures that only the private key owner can access specific data, offering a high level of data privacy and security in various applications, including cloud storage, digital evidence vaults, and personal data management in DApps.
- Other: Privacy is also relevant in fields like on-chain communication, gaming, art, digital media, and, of course, transactions.
The following sections will cover some of the newer privacy projects in Web3. Those projects were born out of this narrative the crypto community has cultivated over the years in response to aggressive regulatory headwinds and the maturing needs of the users. Therefore, let’s look at new privacy projects with this narrative as the backdrop.
Privacy Pools: Addressing Regulatory Concerns
Privacy Pools is an on-chain privacy-enhancing protocol pioneered by researchers, including Ethereum co-founder Vitalik Buterin. Privacy Pools enable users to reveal specific properties about their transactions while keeping direct details of the transaction hidden. Such a primitive can potentially help find common ground between the right to privacy and regulatory compliance.
What are Privacy Pools?
Privacy Pools allow users to obfuscate the origins of their assets using an on-chain mixing protocol similar to Tornado Cash. It is an extension of the design behind Tornado Cash where instead of complete obfuscation, the users have the means to reveal certain details about their funds.
One of the primary issues with Tornado Cash was that the protocol allows the anonymity set of each transaction to potentially equal the entire set of all previous transactions. Therefore, there is no means for an ethical transaction originating from a legitimate source to differentiate from an illicit transaction from, say, a protocol hack.
The protocol works with the help of association sets, which are groups of previously made deposits. When new depositors enter the privacy pool protocol, they claim membership to an association set believed only to comprise ethical deposits. By zero-knowledge-proving that a particular transaction stems from an honest association set, the user can prove their funds come from a legitimate source without revealing any further details about the fund.
Rationale
The rationale behind why this protocol works is that illicit addresses and funds are typically general knowledge due to the public nature of blockchain technology. Whenever a DeFi protocol is hacked and funds drained, we can view this activity on the chain and identify the public address.
All users with “good” assets have an incentive to associate with one another and form a large association set only consisting of “good” funds. The larger the set, the greater the privacy for each participant. When a bad actor, like an exploiter with stolen funds, attempts to join a strong, “good” association set, the set participants already know the funds originate from an illegitimate source and can simply reject its membership.
Benefits of Privacy Pools
- Privacy Pools are an effective solution that promotes ethical privacy. The protocol adopts a simple yet unique selection mechanism that deters “bad” assets from entering the system. It addresses the most vocal argument raised by regulators of allowing defaulters and illicit funds to use mixing protocols to mask their on-chain footprint.
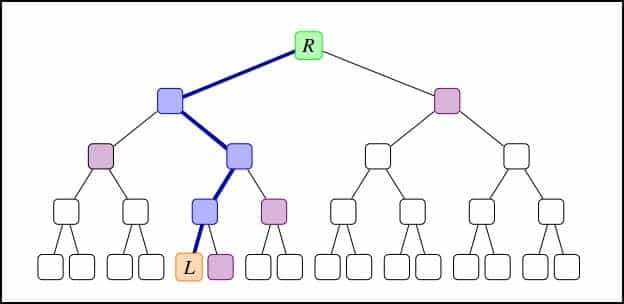
- Privacy Pools use Merkel trees, a system of nesting blockchain transactions to form association sets, and zk proofs to prove membership of an association set privately. Merkel trees give users the unique ability to reveal fewer or more details about their transactions, further broadening the protocol use cases. For instance, consider a user required to report their transactions to authorities for filing taxes while also maintaining their anonymity with the general public.
- In this case, the user can leverage Merkel trees to further elaborate on their on-chain activities in a trusted environment, enabling them to meet their financial obligations without revealing their transactions with the general public, a provision already in practice in traditional finance.
Silent Protocol's Composable Privacy
Silent Protocol is a privacy enhancement protocol that offers functional privacy solutions for layer 1 networks that do not have such measures built in, like the Ethereum network. Silent Protocol positions itself on the client side of decentralized applications. Clients (also known as endpoints) are the user interface allowing users to interact with different smart contracts that make up any Dapp. Clients are not typically part of the blockchain framework. They are usually domains managed by centralized services like AWS and can pose a privacy threat if they are not built securely.
Silent Protocol 0dapps
0dapps are client-facing applications built by the Silent Protocol that enable users to interact with any existing smart contracts of Dapps in a privacy-preserving manner. Users access DApps via Silent Protocol’s EZEE framework, which allows them to access the smart contract operations without revealing the user’s public address, or the fact that they used a specific DApp or smart contract.
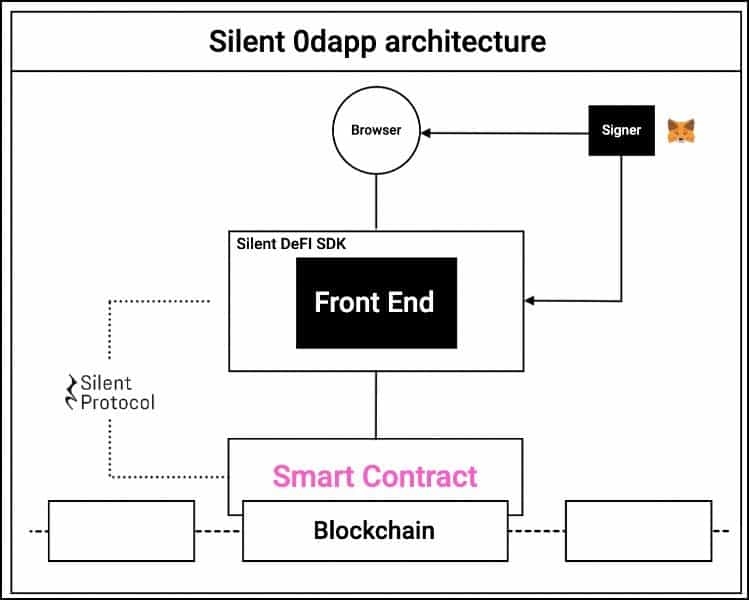
Composable Privacy
One of Silent Protocol's core tenets is composable privacy. One issue with building privacy-preserving systems is that the obfuscated nature of on-chain operations makes it very difficult to chain smart contract calls (use the output of one contract as the input for another). Silent Protocol enables composable privacy by executing the smart contracts in a siloed execution environment, which means it can plug into any existing smart contract framework and enable private execution. 0dapps also maintains the properties of data immutability and public verifiability alive with the help of zero-knowledge proofs.
Secret Network: A Fully Functionally Private Ecosystem
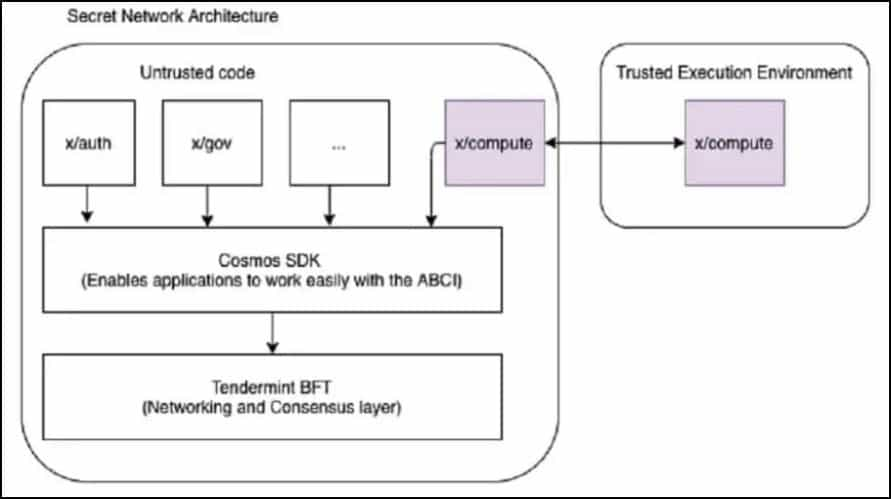
We discussed the concept of fully functional privacy, where everything, including the addresses involved and the tasks performed, is made private. We also covered why legacy protocols are not built to accommodate absolute functional privacy. Secret Network is a layer-1 network built to offer exactly that, programmable privacy capable of hiding all aspects of on-chain interactions.
Secret Network runs on a trustless component and a trusted component. The trustless component is Tendermint which defines its core operations like networking and consensus. The trusted component comprises enclaves, which are a trusted execution environment for the private processing of smart contracts. Enclaves work by executing smart contracts and sending the encrypted data to Tendermint for consensus.
Top projects in the Secret Ecosystem include the Shade Protocol DeFi suite with ShadeSwap, a cross-chain interoperable and front-running resistant DEX with privacy-preserving trades, and the SILK stablecoin and lending protocol. Stashh is an NFT marketplace that serves a thriving ecosystem for NFTs with private metadata.
Parting Thoughts
This article embarked on an analytical journey to introspect upon the evolution of privacy in Web3. After observing the various trends unfolding in the crypto space and understanding the narrative shift users have cultivated over the last few Bitcoin halving cycles, I can draw some interesting parallels from privacy in the real world.
The recent development in on-chain privacy seems to build towards equating the privacy of cash transactions. Cash transactions are free from government oversight and comprise most of our daily currency exchange. The experience of cash transactions and their privacy can be applied on a chain with privacy-preserving transaction protocols. Functional privacy is a more nuanced concept that takes real-world privacy a step further.
Financial privacy is paramount for building advanced financial services like insurance to ensure one's private information is not publicly available on the blockchain. Privacy protocols also work like the on-chain versions of HTTPS and VPS, priming Web3 to address any privacy requirements to migrate social networks, communication channels, and other online activities to Web3. The right to privacy in Web3 is fundamental for the possibility of a future where the term “Internet” will inherently refer to blockchain systems.
Frequently Asked Questions
Privacy Pools are mechanisms that enhance transaction privacy by mixing multiple transactions together. This process obfuscates the trail of individual transactions, making it challenging to trace the original sources and destinations of the funds. Privacy Pools are typically utilized in privacy-focused cryptocurrencies to provide users with an added layer of anonymity in their financial transactions.
The Silent Protocol is a blockchain-based initiative focusing on enabling pseudo-functional privacy. It aims to enhance the privacy of activities on a blockchain network, particularly for Ethereum-based applications. While it doesn't fully conceal all user activities due to the inherent transparency of Ethereum's architecture, it adds a significant layer of privacy over the existing framework, masking certain aspects of user interactions and smart contract operations.
The Secret Network is a blockchain platform that specializes in privacy-preserving smart contracts. It allows developers to build decentralized applications (dApps) that can utilize encrypted data without revealing it on the blockchain. This feature provides a high level of privacy for both transaction details and the operational aspects of smart contracts, enhancing functional privacy and data security in the blockchain ecosystem.
Over the years, the narrative around privacy in blockchain has shifted from a binary view of privacy (either complete privacy or none) to a more nuanced understanding of privacy as a spectrum. This evolution acknowledges varying degrees of privacy needs and types, such as data privacy and functional privacy. The focus has expanded from merely concealing transaction details to also hiding user actions and interactions, reflecting a deeper appreciation for the complexities and ethical implications of privacy in the digital realm.
Blockchain privacy, a key feature in the evolution of digital technology, faces several controversies:
- Illicit Activities: Privacy-focused cryptocurrencies are often used for illegal transactions, such as money laundering, darknet purchases, and financing terrorism, due to their ability to anonymize users.
- Regulatory Challenges: These privacy features conflict with standard financial regulations like KYC (Know Your Customer) and AML (Anti-Money Laundering), making it difficult for authorities to monitor and regulate transactions effectively.
- Exchange Delisting: Facing regulatory pressures, some cryptocurrency exchanges have delisted privacy coins, sparking debates about censorship and the role of centralized platforms in decentralized technologies.
- Privacy vs. Ethics: The protection of user privacy, while a fundamental right, also creates a shield for unethical activities. This raises ethical questions about the extent and implementation of privacy in blockchain technologies.
- Tornado Cash Incident: The sanctioning of Tornado Cash by the U.S. Treasury for allegedly facilitating money laundering highlighted the complex legal and ethical challenges surrounding decentralized privacy tools.
- Blockchain Forensics Complications: Privacy-enhancing technologies make it harder for blockchain forensics to track and analyze transactions, complicating efforts to investigate financial crimes and track stolen funds.
- Transparency vs. Privacy: In applications like supply chain tracking or voting systems, the need for transparency can conflict with privacy, posing challenges in finding a balance between accountability and user protection.
Blockchain privacy has evolved significantly over the years, marked by several key milestones that have shaped its current landscape:
- Introduction of Bitcoin (2009): Bitcoin brought the concept of pseudonymity to digital currencies. Transactions are recorded on a public ledger, offering transparency while keeping the identities of the parties involved obscured. However, this pseudonymity is limited, as transaction patterns can potentially be analyzed to expose user identities.
- Darkcoin/Dash (2014): Originally named Darkcoin, Dash introduced features like PrivateSend, which enhanced privacy by mixing transactions. This made it more difficult for observers to trace individual transactions back to their sources, addressing some limitations of Bitcoin's pseudonymity.
- Monero (2014): Monero took privacy a step further by using ring signatures and stealth addresses to obfuscate transaction details. This made Monero transactions virtually untraceable, establishing it as a leading privacy coin.
- Zcash (2016): Zcash introduced ZK-SNARKs (Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge), allowing transactions to be validated without revealing any information about them. Users could choose between transparent and shielded transactions, influencing many subsequent privacy-focused projects.
- Verge (2016): Verge focused on IP address privacy, integrating technologies like Tor and I2P to obscure users' IP addresses, adding another layer of privacy to cryptocurrency transactions.
- Beam and Grin (2019): Both built on the Mimblewimble protocol, Beam and Grin offered enhanced privacy and scalability. Mimblewimble's main feature is its ability to combine multiple transactions into one, reducing blockchain size and increasing privacy.
- Secret Network (2020): Secret Network introduced privacy-preserving smart contracts, allowing developers to create decentralized applications (DApps) using encrypted data without revealing it on the blockchain. This expanded blockchain privacy from transactions to complex applications.
Disclaimer: These are the writer’s opinions and should not be considered investment advice. Readers should do their own research.


