Oasis Protocol Review: The Private & Scalable Blockchain!
Blockchain network designs never draw in the reins of innovation. The Bitcoin network was born as a simple peer-to-peer network to store and transact value. The success of Bitcoin sowed the seeds of the Ethereum decentralized network and its smart contract capabilities and marked the birth of DeFi.
Soon, the monolithic blockchain network proved inadequate in quenching the hunger for block space. Vitalik Buterin conceptualized the scalability trilemma in the late 2010s to highlight the trade-offs between decentralization, scalability, and security. Innovators soon began experimenting with multi-layered blockchain systems that offloaded the stress of the mainnet to side chains, state channels, rollups, and lightning networks to make blockchain accessible for day-to-day transactions.
The Rise of Modularity
The blockchain community had begun to embrace the idea of a modular blockchain architecture by the early 2020s. Modularity abstracted the blockchain infrastructure into layers like consensus, data availability, and execution; decoupling these components into separate layers allowed circumventing the scalability trilemma to offer higher throughput while maintaining the initial security guarantees.
The Ethereum ecosystem evolved towards inter-blockchain modularity with rollups like Optimism and Arbitrum, handling execution off-chain. Projects like Polkadot and Cosmos introduced the “blockchain of blockchains,” where various blockchains could interoperate but operate independently.
This Oasis Network review will cover a blockchain network that adopts an intra-blockchain modular design, another flavor in the story of layered architectures attempting to balance scalability, security, and decentralization. Let’s dive in!
Oasis Network Overview
The blockchain industry is evolving towards modular architectures. The ‘rollup-centric roadmap’ solidifies Ethereum as the data availability and security layer of DeFi in which modular execution environments exist as rollups and host smart contract applications.
The Oasis Protocol experiments with three major design themes:
- Native modularity – Ethereum is natively monolithic. Rollups achieve modularity with an off-chain network that attests its state transitions to a rollup smart contract deployed on the Ethereum mainnet. The Oasis Protocol offers native modularity. Instead of smart contracts, the blockchain nodes implement modularity at the infrastructure level.
- Privacy-preserving smart contracts – Oasis enables verifiable and confidential smart contract execution to promote applications that handle private and sensitive data like social recovery numbers and bank accounts, where the data only concerns a small number of individuals.
- Data Tokenization - Leveraging smart contracts to facilitate tokenized private data that maintains privacy and security standards.
Oasis Protocol Background
Dawn Song, a professor at the University of California, Berkeley, known for her work in computer security and artificial intelligence, initiated the Oasis Labs and began working on the protocol. The Oasis Foundation was also created independently of the Oasis Labs to promote the Oasis ecosystem's empowerment, governance, and decentralization.
The Oasis Network is unique in its focus on privacy and data tokenization. The protocol perceives privacy as a tool to mobilize data for analytics in a decentralized setting rather than obscure transactions to hide a user’s identity. Oasis Protocol seeks to enable selective sharing so that individuals can monetize their data while retaining its access and privacy rights.
The Oasis team launched the private testnet in 2018 and the public mainnet in 2020 after multiple audits, bug bounties, and network upgrades. The protocol is backed by esteemed venture capital firms and investors like Binance Labs, Polychain Capital, Pantera, and Andreessen Horowitz (a16z).
What is the Oasis Protocol?
The Oasis Network is designed as a privacy-focused, layer-1 Proof of Stake (PoS) smart contract capable decentralized network compatible with the Ethereum Virtual Machine (EVM). It deploys a modular, multi-layer architecture with a separated consensus and execution layer (called ParaTime Layer).
The Oasis network design is akin to the rollup architecture. In the Ethereum ecosystem, rollups are high-throughput execution environments. They package their rollup transactions into bundles and submit them to the Ethereum mainnet to make that data available during the Ethereum consensus and thus borrow its security. Rollups use smart contracts deployed on the mainnet to their blockchain data. This design is linearly scalable, meaning we can add new rollups for better scalability or add new functionality without affecting the operation of other rollups, and all rollups are processed in parallel.
The Oasis network offers high scalability using a similar design. The Oasis blockchain mainnet is a Proof-of-Stake network offering consensus and data availability to the ParaTime layers. The ParaTimes are where smart contract functionality occurs, with all the parallel execution and linear scalability of Ethereum.
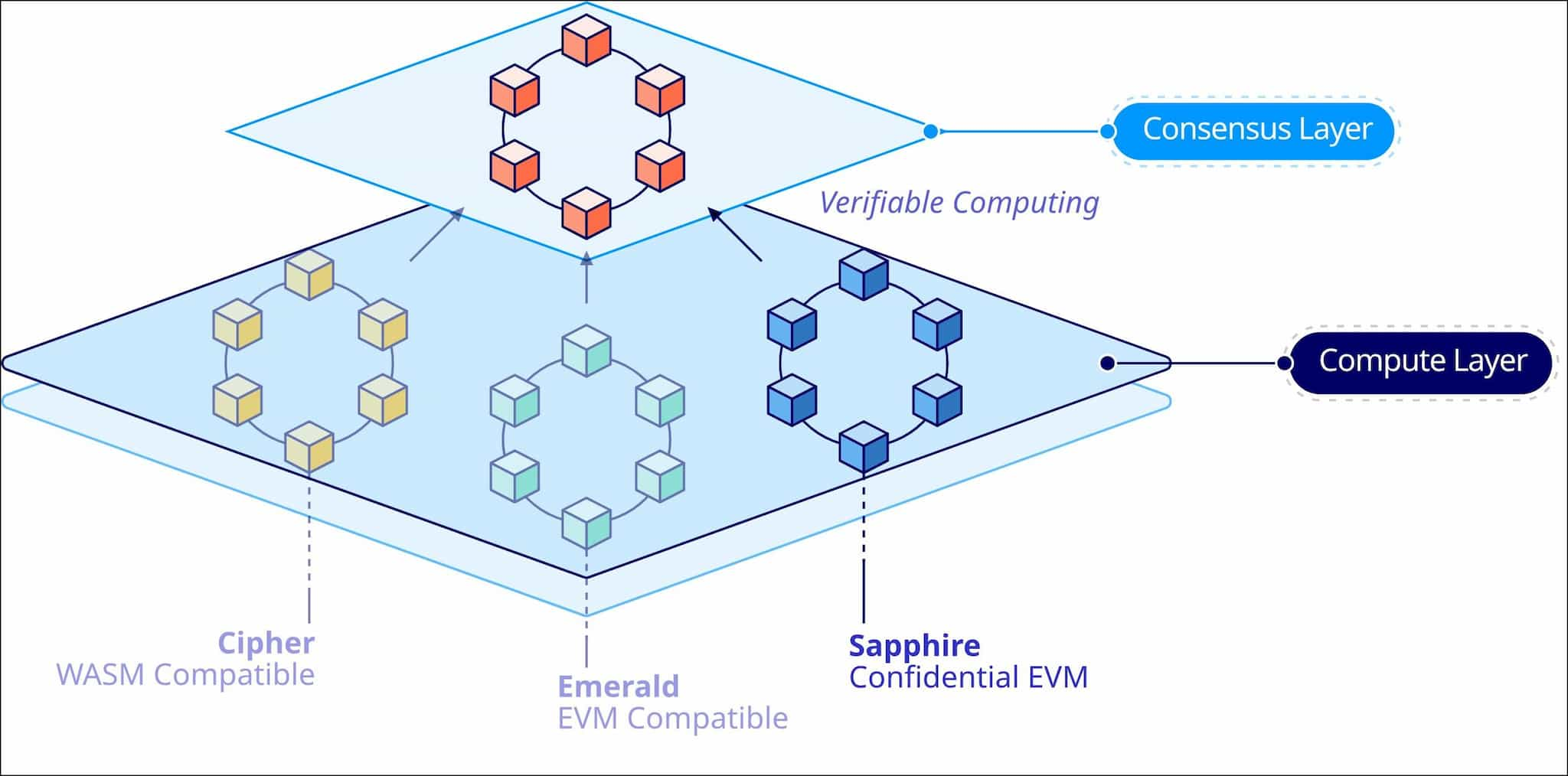
Oasis Network Architecture
The Oasis Network technology comprises the following major components:
The Oasis Network Consensus Layer
The Consensus Layer forms the foundation of the Oasis Protocol and performs the following essential functions:
- It accepts values from the ParaTime layer and writes them on the consensus layer.
- It performs ParaTime and validator selection.
- Consensus layer native token operations.
The Consensus layer is the security layer of the Oasis ecosystem. Each block comprises a limited number of ParaTime layer transactions, providing them finality by accepting and storing their data during block production. Note that the Consensus layer does not attempt to interpret the complex workloads of the smart contract logic, like the generated values or the computations executed within the ParaTime layer. Instead, it is more about ensuring those transactions' overall security and finality.
While the ParaTime layers handle the execution of transactions, the Consensus layer deals with transaction ordering and integrity to ensure a secure architecture.
The Consensus layer also handles the ROSE native transactions executing on the base layer. The Consensus layer is a Proof-of-Stake network running on the Tendermint core, but its simple functionality allows Oasis Protocol the liberty to replace it with other consensus models, like Lira HotStuff, if required, with minimal impact on the modular system.
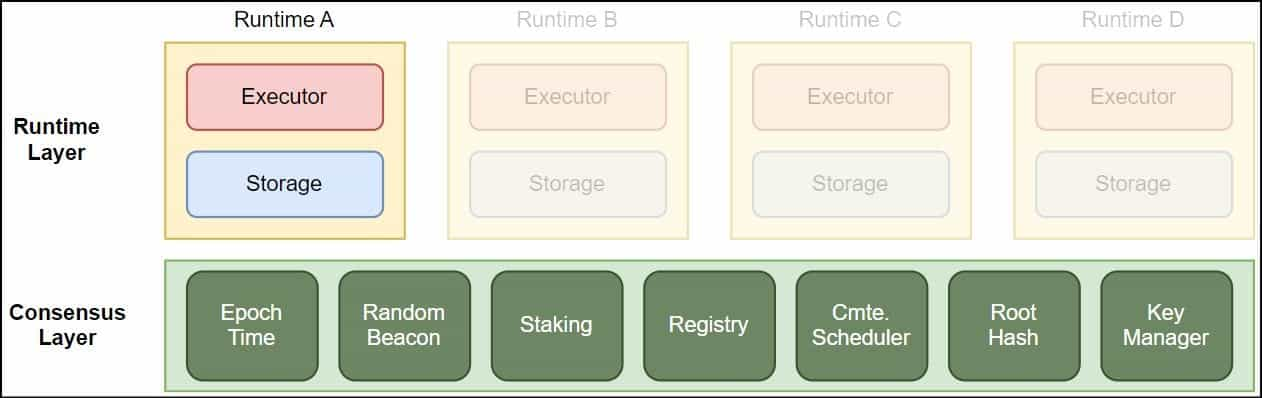
ParaTime Layer
The ParaTime layers are where smart contract execution occurs. The Consensus layer can support multiple ParaTimes that can operate parallel runtimes. Like Ethereum hosts several rollups like Optimism and Arbitrum operating in isolated silos, the state transitions of one ParaTime do not affect the others.
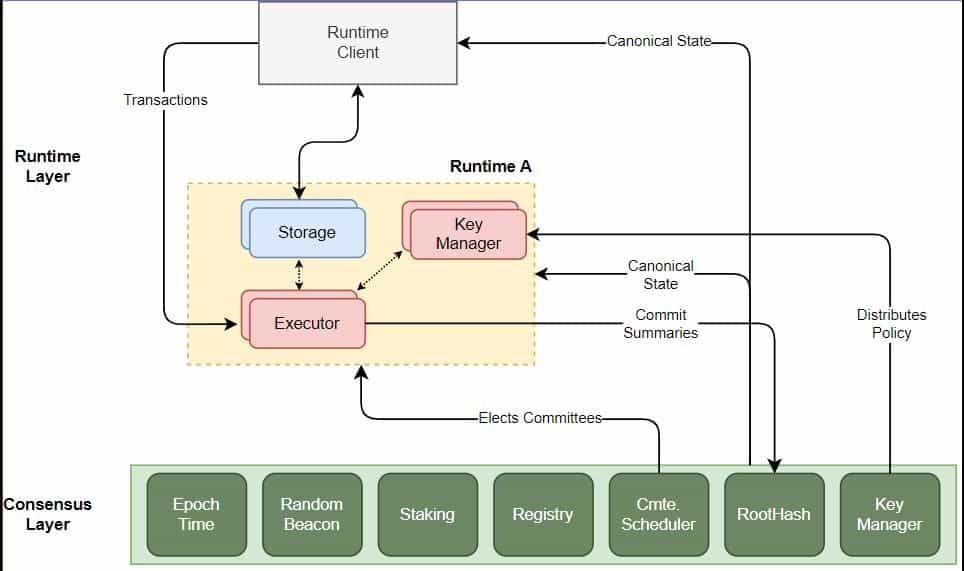
ParaTimes execute state computations and commit the result to the consensus layer, which stores a canonical summary of these state transitions. Like any blockchain protocol, the ParaTime also runs on nodes. These nodes process transactions from clients and register on the consensus layer to participate in the operation of the desired ParaTimes.
This participation enables protocol-level integration of the ParaTimes and the consensus layer, which Oasis believes is more efficient than other modular designs, like Parachains and sharding.
ParaTime Operational Model
- The ParaTimes are created by developing their code and specifying their metadata. Each ParaTime is allocated a runtime identifier during registration.
- A Node operator runs the ParaTimes to execute its procedures. They process transaction requests from clients. They also maintain adequate space to store ParaTime state. The validator nodes that run ParaTimes and the ones that store the state may also be different.
- Such a node operator then registers on the consensus layer.
- A client can submit ParaTime transactions by publishing the transactions to the appropriate node on the consensus layer that runs the corresponding ParaTime.
- The consensus layer finalizes the transactions after verifying that the computation was performed correctly.
Separated consensus and execution layers allow multiple ParaTimes to scale without worrying about security and enable parallel processing of different ParaTimes together. Oasis can host different kinds of ParaTimes to address various use cases. One such application is hosting EVM-compatible ParaTimes to support Ethereum applications or ParaTimes with confidential smart contracts processing to support Data analytics applications. The modular design allows the ParaTimes to update independently of the consensus layer or other ParaTimes.
Oasis Network ParaTime Layers
The Oasis core developer team has already developed three ParaTimes on the network:
Oasis Network Emerald EVM Compatible ParaTime
The Emerald ParaTime layer is an Ethereum Virtual Machine (EVM) compatible blockchain network in the Oasis Network. Emerald is built to integrate Ethereum-compatible smart contracts on Oasis easily. Here are the key features of Emerald:
- Fully EVM-compatible
- High throughput and low fees
- Scalable. With an average block time of just under 25 seconds, Emerald can boast high throughput and low transaction fees.
- Decentralization – Emerald is operated by a decentralized node network that secures the network with ROSE as the settlement currency.
Oasis also runs a reward program for node operators on Emerald. The ParaTime releases on-chain tokens to reward validator nodes for participating in the network. The program rewards up to 24 ROSE tokens per day to each node. The two-year-long reward program began in November 2021.
Oasis Network Cipher Confidential ParaTime
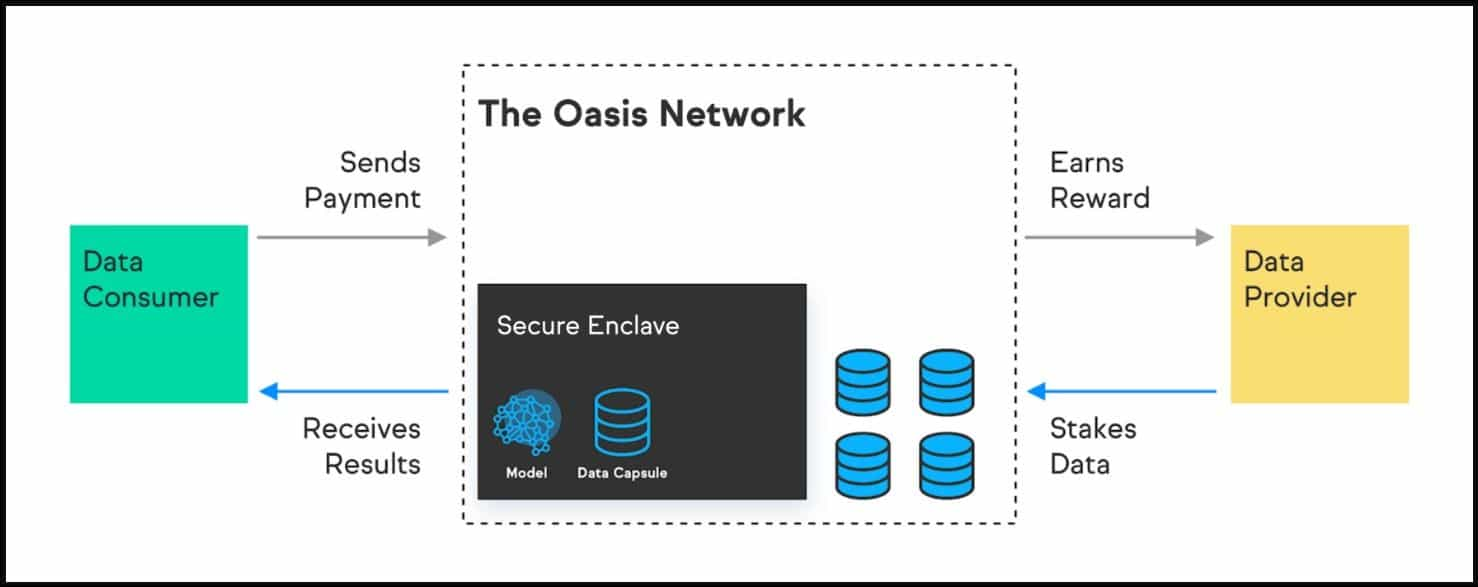
Confidential smart contract execution is one of the primary deliverables of the Oasis Network. The Cipher Confidential ParaTime layer supports high throughput smart contract execution privacy where nodes use a Trusted Execution Environment (TEE) computing technology.
Trusted Execution Environment works like a hypothetical black box for smart contract execution, where the encrypted data enters a secure enclave with the smart contract. The encrypted data is then decrypted inside the enclave to prime it for processing by the smart contract code. Finally, the results are encrypted before they are sent out from the enclave so that data remains confidential.
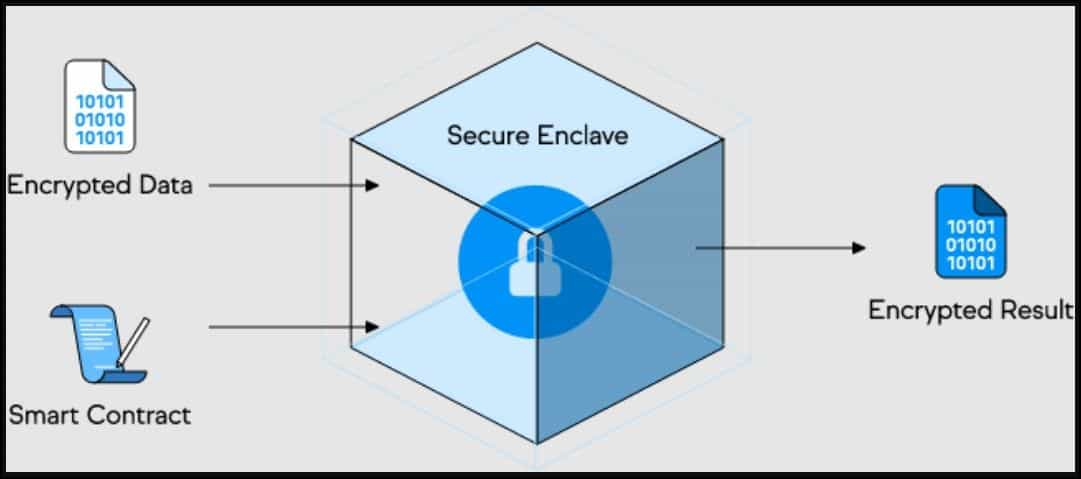
Cipher ensures that the data is never leaked to node operators, application developers, or any third party. Confidentiality is vital in introducing data management services in a decentralized setting. For instance, an application developer on the Oasis protocol may use personal or sensitive data like social security numbers, financial or health information, or geographical records as processing inputs. Confidentiality of such data concerns the data owners and does not obscure the security or openness of the blockchain protocol.
With Oasis, general users like you and I can monetize our data in a secure and private environment while retaining complete control over its access and use at the same time.
The Oasis network offers further modularity by enabling developers to use other privacy-preserving technologies like Zero-Knowledge Proofs to power private enclaves, enabling customizable confidentiality to developers.
Tokenized Data – Oasis enables the new paradigm of data tokenization, where the protocol ensures that data remains private and inaccessible without permission. Allowing for confidential computing of private data creates a new kind of digital asset that can be consumed along with specific guidelines of use for a fee. For instance, this model is helpful for training machine learning software that requires a lot of data, which is often private.
Oasis Network Sapphire EVM Compatible Confidential ParaTime
Oasis Network introduced the Sapphire ParaTime layer to bring the functionality of Cipher and Emerald together with near-instant finality. Sapphire is an EVM-compatible environment for executing confidential smart contracts. Developers from Ethereum that require high levels of privacy to enhance the use cases of their applications can leverage Sapphire without incurring a lot of additional overheads associated with switching platforms.
Oasis Network ROSE – Tokenomics
ROSE is the native utility token in the Oasis Network. On the consensus layer, ROSE powers staking and delegation, used to pay transaction fees for transfers on the mainnet as well as for fees for smart contract execution on the ParaTime Layers.
Token Distribution
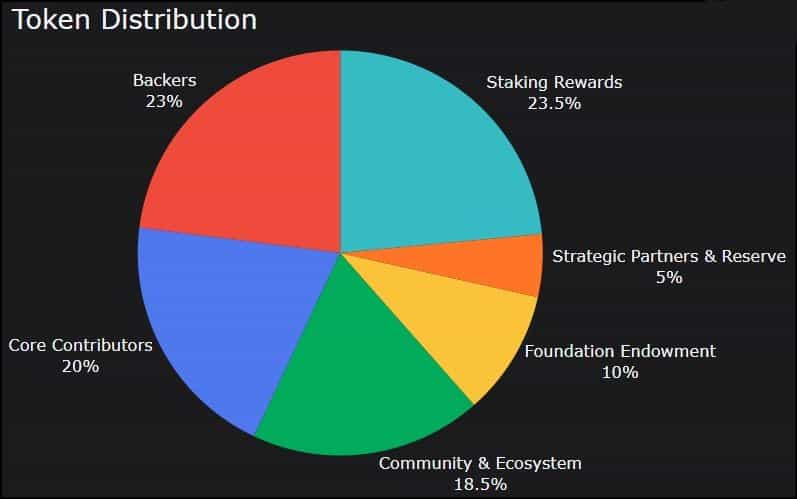
ROSE has a fixed supply of 10 billion tokens, with a circulating supply of about 6.5 billion in October 2023. Here’s how the Oasis team allocates the liquidity:
- Protocol backers were sold tokens prior to the mainnet launch.
- The core contributors received ROSE as compensation for their efforts.
- The Oasis Foundation received some tokens as an endowment for the development of the Oasis Network.
- The community and ecosystem allocation will fund programs that stimulate the community, like developer grants and incentives.
- The key strategic partners of the Oasis Ecosystem are funded for their services.
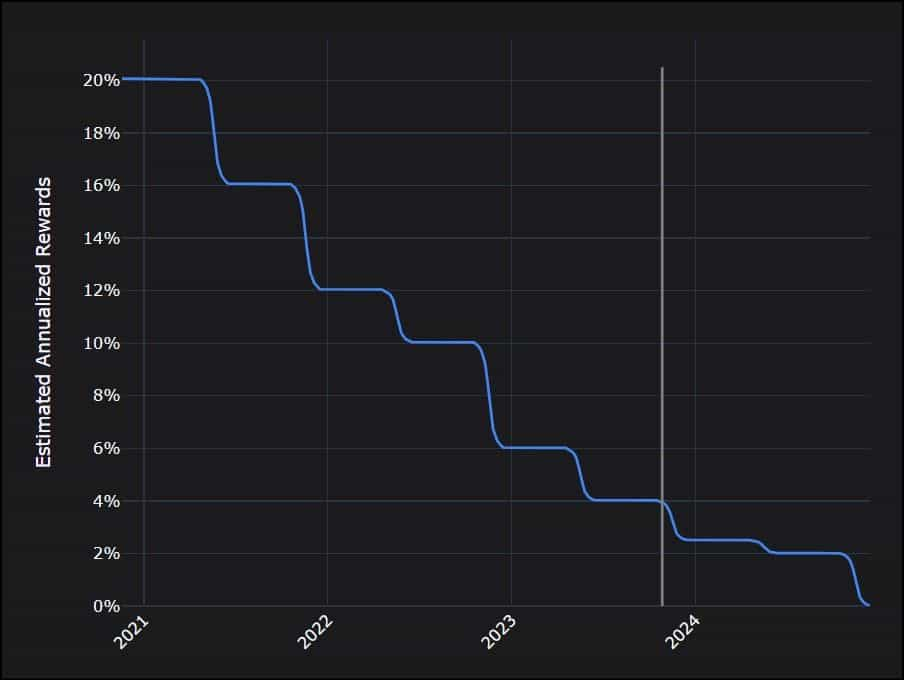
- Staking rewards are paid out to on-chain stakers and delegators for contributing to the security of the Oasis Network. The protocol will calculate rewards based on block production, node participation, and staking patterns to disperse the rewards over four years.
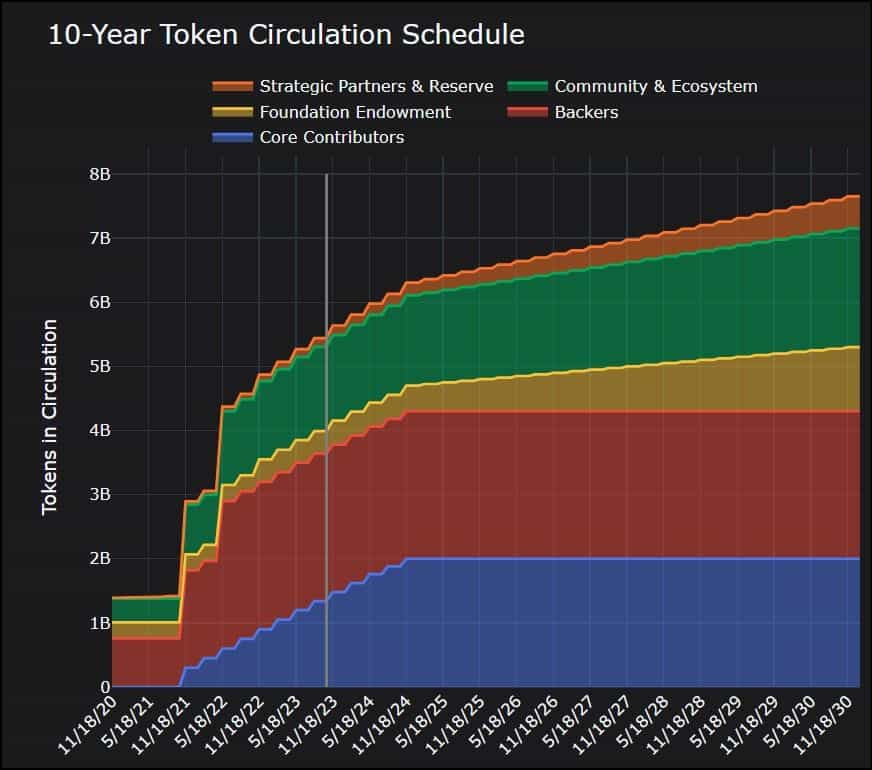
The tokens allocation is subject to a vesting schedule spread over ten years starting in 2020. It will gradually unlock the tokens allocated across the ecosystem, which is illustrated in this chart:
Oasis Use Cases
Oasis Network Use Cases
The Oasis Network adopts an open architecture, making it compatible with several use cases and execution environments. It is built using Tendermint Core, making it easy for developers in the Cosmos Ecosystem to connect to the Oasis Network. The Emerald ParaTime layer on the Oasis network is EVM-compatible, which may attract developers, users, and applications from Ethereum.
- Confidential smart contracts – The ability to execute smart contracts while maintaining the privacy of data inputs and the results is one of the key features of the Oasis Network. This feature can potentially onboard applications that require privacy, such as financial transactions, voting platforms, or applications handling sensitive personal or professional information.
- DeFi – Oasis Sapphire can enable private lending and borrowing, yield farming, and other DeFi protocols.
- Private NFTs – Oasis Network can facilitate private NFT ownership, which may appeal to the art and collectables industry.
- Data Tokenization – The Oasis platform can host secure, privacy-focused data marketplaces where data providers can monetize data and businesses can access valuable data sets without violating the provider’s confidentiality.
- Enterprise data sharing – Enterprises can leverage the Oasis Network to share confidential data securely and privately across its departments and partners, making it relevant in industries like healthcare, legal services, and finance.
- AI and Machine Learning – AI models can have access to valuable datasets to train their models on the Oasis Network.
- Supply Chain Management – The Oasis Network can enhance supply chain efficiency and privacy. Parties can securely and confidently share relevant information across the globe without worrying about information leaks.
- Digital identification systems – Oasis Cipher can support secure and private identity verification processes.
- Governance and voting – The Oasis protocol can facilitate private voting for DAOs.
- Cross-chain messaging – Applications can use Sapphire to relay information between blockchain networks confidentially.
These use cases highlight the potential of Oasis Sapphire in addressing the growing demand for privacy and security in the blockchain space, particularly in sectors where data sensitivity is a major concern. As the technology and the ecosystem around Oasis Network evolve, new applications and use cases will likely emerge.
Projects Associated With The Oasis Ecosystem
The Oasis Protocol has attracted a variety of decentralized applications (dApps) and products across different sectors, leveraging its privacy-centric features and scalable architecture. Here's an overview of some notable dApps and products built on the Oasis Protocol:
- Decentralized Finance:
- YuzuSwap: A decentralized exchange (DEX) offering liquidity pools, yield farming, and token swapping services.
- Lizard Exchange: An automated market-making (AMM) decentralized trading platform with low fees and high-speed transactions.
- Fountain Protocol: It is a lending platform on Oasis.
- Data Privacy and Management - Parcel provides a set of privacy-first, data governance APIs designed to give your users better control over how their data is used without sacrificing functionality.
- NFT and Gaming - tofuNFT, an NFT marketplace on Oasis Emerald. It lists several NFT projects on Oasis, like Oasis Kops, Oasis Punks, and Drift Souls.
- Enterprise Solutions - Oasis Labs is working with Binance and other members of the CryptoSafe Alliance to develop a decentralized CryptoSafe Platform, enabling the alliance members to share and access threat intelligence data across exchanges.
- Healthcare Applications - Nebula Genomics, a genome sequencing service provider, has partnered with Oasis Labs to give users more control over their data and enhance their security on its privacy-preserving personal genomics platform.
- Healthcare Data Marketplaces - There are initiatives to use Oasis for secure and private healthcare data exchanges, enabling research and development while protecting patient privacy.
- Cross-Chain and Interoperability Solutions - The Wormhole Bridge is a cross-chain bridge connecting Oasis with other major blockchain networks, facilitating asset transfers and interoperability.
- Identity Verification and Security - Celer, a blockchain interoperability protocol that operates the cBridge has integrated with Oasis Sapphire to enable cross-chain bridge through its network.
It's important to note that the blockchain and crypto space is highly dynamic, and new projects and partnerships are frequently announced. The Oasis Protocol, with its focus on privacy and scalability, is particularly attractive for applications that handle sensitive data or require high throughput. As the ecosystem grows, we can expect to see a wider range of dApps and products emerging on this platform.
Projects choose the Oasis Protocol primarily for its unique combination of privacy features and scalability. Oasis offers confidential smart contracts, enabling developers to build applications that can process sensitive data securely without exposing it, a crucial aspect for sectors like finance, healthcare, and enterprise solutions.
Additionally, its high throughput and low gas fees make it an attractive platform for DeFi applications, NFT marketplaces, and gaming, where transaction speed and cost-efficiency are key. The protocol's compatibility with Ethereum also facilitates easy migration and interoperability for developers already familiar with Ethereum's ecosystem. This blend of privacy, performance, and developer-friendly environment makes Oasis an appealing choice for a wide range of blockchain applications.
Oasis Wallet Support
The Oasis network supports two non-custodial wallets:
- The Oasis Web wallet.
- The Oasis wallet browser extension.
Features of the Web Wallet
- Accessibility: Accessible through a web browser, making it easy for users to manage their assets from any device with internet access.
- User Interface: Typically offers a user-friendly interface for managing assets, viewing transaction history, and interacting with the Oasis Network.
- Basic Functions: Allows for basic wallet functions like sending and receiving the network's native token and other supported tokens.
- Security: While convenient, web wallets generally are less secure than hardware wallets because they are more susceptible to online threats.
Features of the Browser Extension Wallet
- Integration with Web Browsers: Designed as an add-on for web browsers like Chrome or Firefox, offering a more seamless experience for web-based interactions.
- Enhanced Security: Often provides better security than web wallets, as they can enable more secure interactions with web applications while reducing exposure to phishing sites.
- Convenience for DApps: Ideal for frequent interactions with decentralized applications (DApps) on the Oasis Network, as it can easily connect and sign transactions.
- User Experience: Provides a more integrated experience for users who regularly use DApps or participate in DeFi activities on the Oasis Network.
Adding Oasis Network to MetaMask
Adding The Oasis Network to your MetaMask wallet is straightforward. Check out our guide on using MetaMask wallets if you are unfamiliar. If you already have a MetaMask wallet installed on your browser, visit the Oasis Network Ecosystem page to add Emerald and Sapphire with just one click.
How does Oasis Protocol Compare to Other Platforms?
| Feature | Oasis Protocol | Ethereum | Polkadot | Ocean Protocol | Secret Network |
| Consensus Mechanism | Proof of Stake | Proof of Stake | Nominated Proof of Stake (NPOS) | Proof of Stake | Tendermint consensus |
| Privacy Features | Strong focus on privacy with confidential ParaTimes | Limited, relies on layer-2 solutions | No inherent privacy feature | Focus on data privacy and secure data sharing | Privacy for smart contracts, secret contracts |
| Scalability | High scalability with a modular design | Improved scalability with layer-2 and sharding | High scalability through Parachains | Moderate, depending on the Ethereum Network | Scalability similar to Ethereum |
| Smart Contract Support | Yes, with ParaTimes | Extensive, with Solidity and Viper | Yes, through Parachains | Limited, focus on data tokens and marketplaces | Yes, with secret contracts for privacy |
| Interoperability | Limited, compared to other competitors | Limited, relies on bridges and layer-2 chains | High, with cross-chain communication via relay chain | Interoperability via Ethereum | Primarily operates within the Ethereum ecosystem |
| Governance | On-chain | On-chain | On-chain | DAO driven | Dependent on Ethereum |
| Use Cases | Privacy-focused dApps, DeFi, data tokenization | DeFi, General blockchain applications, Web3 | Interoperable Appchains | Decentralized data marketplaces, data sharing | Privacy-preserving computation, secure data processing |
| Developer Ecosystem | Growing, with an emphasis on privacy-preserving applications | Very large and active | Growing and diverse due to Parachains | Focused on data and AI-related applications | Niche, focused on privacy-enhanced computations |
| Transaction Fees | Generally low | Volatile | Depends on the Parachain | Dependent on Ethereum | Dependent on Ethereum |
Oasis Protocol Roadmap
Oasis Protocol has made significant strides in achieving its outlined goals and objectives in its roadmap.
- Oasis Privacy Layer (OPL) Launch: The Oasis Protocol successfully launched the Oasis Privacy Layer (OPL) in 2022. The OPL empowers developers to add privacy elements to any dApp on any EVM chain while preserving the user experience
- Trustless Bridge to Ethereum: The Oasis Network has integrated with powerful blockchain protocols and toolings like Covalent and Band Protocol, improving the developer and user experiences of community-built projects.
- Network improvements with the Core 23.0 upgrade: The Core 23.0 upgrade introduced several key improvements.
- Node Operator Experience: Improves user experience for node operators with enhanced security and efficiency, including peer-to-peer network state sync for easier node initiation.
- Governance Expansion: Allows delegators to vote in governance, not just validators, broadening democratic participation. Supports voting on a wider range of proposals, including parameter changes.
- Key Rotation Security: Introduces ephemeral key rotation every epoch for increased transaction security and supports daily state key rotation for ParaTimes.
- ParaTime Enhancements: Upgrades ParaTimes with reduced query latency and instant future runtime upgrades, improving overall performance and robustness.
- Oasis Wallet User Experience Improvements: The Oasis Network leveraged Metamask to improve the wallet experience, which now supports Emerald and Sapphire.
- Community Engagement: The Oasis Network has successfully fostered a thriving and rapidly growing community of node operators, developers, enterprise partners, ambassadors, and community members engaged in global social channels. They have hosted inspiring hackathons and connected with Web3 communities across the globe at the industry’s most important events to drive growth across the entire network.
In addition to these, the Oasis Network has formed strategic partnerships with industry-leading companies like Meta and Equifax, and its ecosystem fund grew from $160 million to $235 million with support from new partners.
Oasis Protocol Review: Summary
This review began with an exploration of blockchain modularity and its significance in helping blockchain networks achieve the throughput and security standards needed for global mainstream adoption. The Oasis Network adds a unique flavor to this design architecture with intra-blockchain modularity and amplifies the concept by introducing data tokenization and confidential smart contracts.
Projects like the Oasis Network reimagine the operational designs of industries that have been around for decades, making them more efficient using distributed networks. These projects cement the reputation of Web3 as a groundbreaking innovation that does not merely exist in its own virtual bubble but has the potential to tap into the oldest roots of the global economy.
Frequently Asked Questions
Oasis Protocol is a privacy-focused blockchain platform known for its unique two-layered, intra-modular architecture: the Consensus Layer and the ParaTime Layer. This separation allows for enhanced privacy and scalability. Unlike many blockchains, Oasis specializes in confidential computing, enabling secure data processing and privacy-preserving applications, making it ideal for use cases in finance, healthcare, and other sensitive data-driven sectors.
Oasis Protocol ensures privacy through its ParaTime Layer, which supports confidential smart contracts and secure data processing. This layer uses advanced cryptographic techniques, like secure enclave technology, to execute computations on encrypted data, ensuring data privacy and security. This approach allows users to share and compute data without exposing the actual data, setting Oasis apart in its ability to handle sensitive information.
Yes, developers can build applications on the Oasis Protocol, leveraging its privacy features and scalable architecture through EVM-compatible confidential smart contracts. The platform is designed to be developer-friendly, offering tools and resources to create decentralized applications (DApps), especially those requiring data privacy. With its focus on confidentiality and security, Oasis is particularly attractive for developers in fields like decentralized finance (DeFi), healthcare, and data tokenization.
Disclaimer: These are the writer’s opinions and should not be considered investment advice. Readers should do their own research.


