Navigating the Ethereum roadmap reveals a complex journey of development and innovation. It is a complex web of protocols and systems that are constantly refined and improved upon. And like most engineering problems, the first solution to a problem is not refined—it is often raw, unpolished, and full of potential waiting to be harnessed. Let's take a trip down memory lane to when the internet was just a fledgling idea to illustrate this concept better.
In the early days of the Internet, it was a niche technology utilized by a select group of highly technical people. It began as a simple network, ARPANET, designed to facilitate communication between academic institutions. At this point, the internet was far from the global information superhighway we know today. It was rudimentary, clunky, and limited in its capabilities.
The internet´s journey from a simple network to a worldwide web was fraught with challenges. It required the creation of new protocols like HTTP and HTML, the evolution of dial-up to broadband, and the development of browsers that could decode and present the information found on the web.
Just think about the leap from browsers of the early 90s, like Mosaic shown below, to the modern internet experience.
The internet we know today is a product of numerous technological breakthroughs and adaptations that helped it transition from niche to mainstream. It had to overcome a plethora of technical, regulatory, and cultural challenges to become the ubiquitous force it is today.
In a similar vein, Ethereum started as an empty canvas for innovation, a new frontier for exploring the possibilities of decentralized applications (DApps) and blockchain infrastructure. Among these innovations, decentralized finance (DeFi) has emerged as a pivotal application on Ethereum, revolutionising how we think about financial services and transactions
As the Ethereum community, a brilliant group of developers, technologists, and visionaries, set about building upon this canvas, Ethereum is evolving in a similar fashion as the internet did.
The current state of Ethereum may resemble that of the internet in the late 90s. We are transitioning from a technology used by a few tech-savvy people featuring a user experience with multiple pain points to a platform for the masses. Like the internet started a data center and fiber optic infrastructure push in the late 90s to become scalable and cost-effective, Ethereum is becoming accessible thanks to layer two scaling solutions introduced just a few years ago. This accessibility is a stepping stone towards Ethereum 2.0, which aims to address the scalability trilemma, a core aspect of Ethereum's evolution.
The killer app equivalents like YouTube, social media, and online payments came in the 2000s could be yet to come.
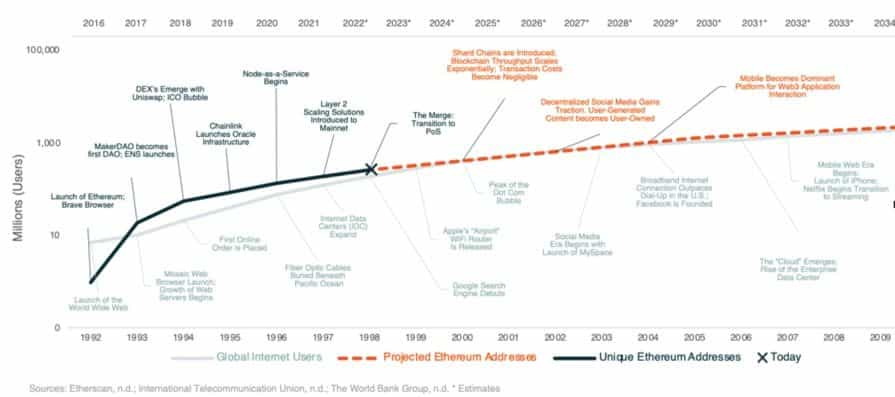
A notable caveat to the similar growth theory is that the internet provides the infrastructure for crypto, and the speed of information transfer is higher than ever. Crypto adoption could happen at an even higher pace, so act accordingly and take good care of your precious coins.
However, as with any engineering problem, the progression of Ethereum is full of challenges. Technical issues become more nuanced and complex as the technology stack becomes more sophisticated. These challenges are no longer about simply making things work but refining, perfecting, scaling, and making Ethereum accessible to everyone.
As we delve deeper into Ethereum's challenges, we turn to the words of founder Vitalik Buterin. In a recent blog post, Vitalik highlighted The Three Transitions Ethereum must undergo to succeed. These transitions illustrate the complexity of the issues at hand and shed light on Ethereum's path to realizing the vision of bringing an open, global, and permissionless experience to the average user. Vitalik discusses that the three major technical transitions that we need to accomplish are:
- The L2 scaling transition.
- The wallet security transition.
- The privacy transition.
Feel free to check out the video below if you want Guy's take on Ethereum in 2023:
1 – The Layer 2 Scaling Transition. Everyone Moving to Rollups
Vitalik believes that without users and applications moving to rollups, Ethereum fails because products aiming for the mass market may have to abandon the chain and adopt centralized workarounds to avoid excessive transaction fees.
Daily transaction fees were as high as $200 at their peak in May 2022 and have since levelled off.
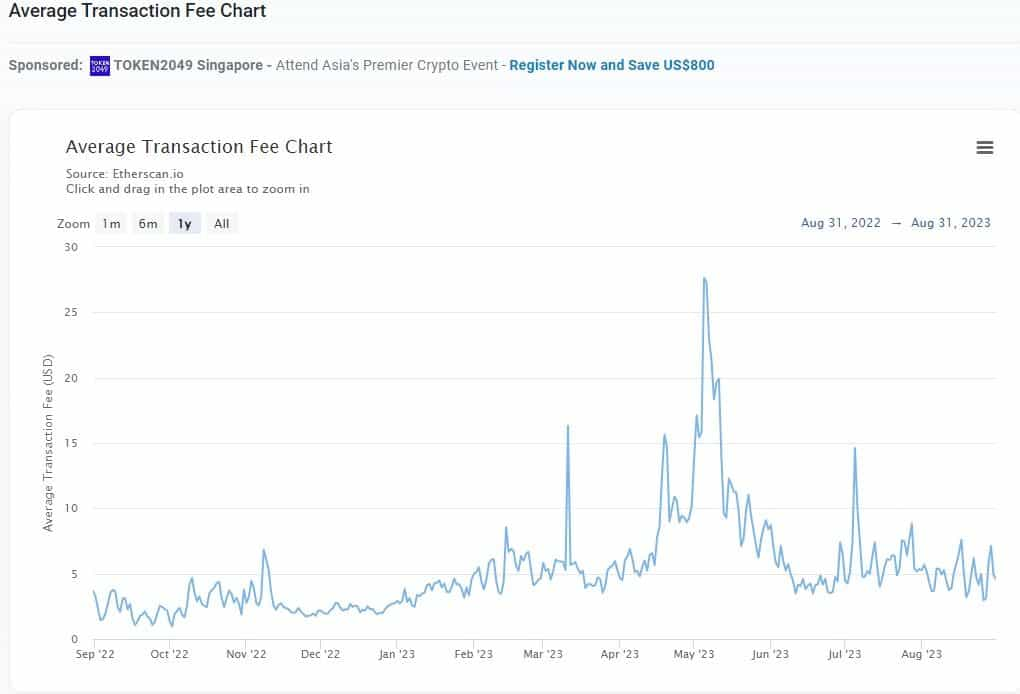
In contrast, Layer 2s (L2s) can process transactions at a fraction of the cost. For instance, sending ETH from one address to another in Optimism would cost a user $0.03, compared to $0.68 on the Ethereum Network.
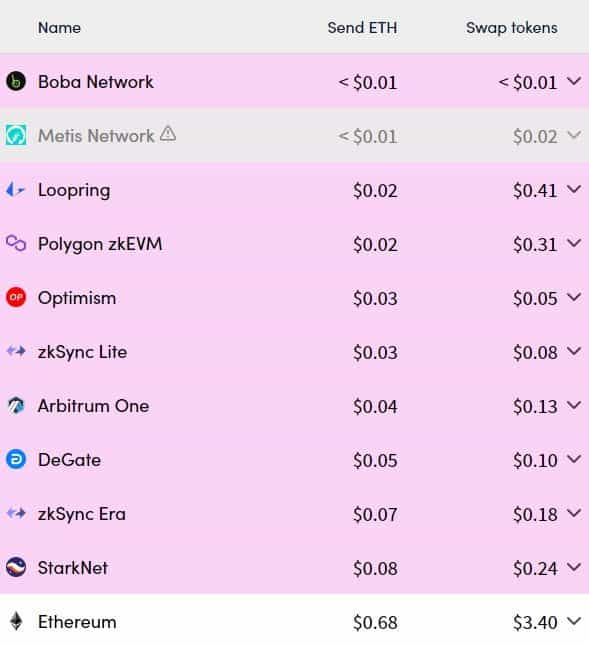
Rollup fees are expected to decrease further by a factor of 20+ once Ethereum shard chains launch – a number that can increase in the future. With shard chains, less-than-a-cent fees could become a reality soon. Unsurprisingly, Vitalik had strongly advocated the technology underpinning rollups as early as 2019, back when rollups were largely conceptual.
What are Rollups?
Chances are that you have already stumbled upon rollups, so feel free to skip this section, but if you don’t live and breathe crypto, here are rollups demystified:
Rollups are smart contract-enabled frameworks built on Ethereum that massively increase the network’s transaction capacity. This is done by performing computation off the main Ethereum chain (Layer 1) and returning only a highly compressed form of the final result of the transactions, known as the state root of the rollup.
The intricate bit proves to Ethereum that the proposed state root is valid. This is done via Fraud Proofs or Validity Proofs, depending on whether the rollup is Optimistic or ZK. Verifying either type of proof is much cheaper than doing the original computation on the Ethereum network, so the resulting system dramatically increases the transaction throughput and reduces costs.
The result is a system that solves Ethereum's scalability issues while maintaining its security and decentralization. Security is maintained as the state of the rollup is available in the Ethereum network, meaning users always have the information necessary to verify transactions. Decentralization isn’t compromised either, as the network scales without increasing the computational load – nodes are as affordable to run as they have always been, and no high-performing hardware is required.
This solution directly addresses the scalability trilemma, balancing scalability, security, and decentralization, which is vital for Ethereum's long-term success.
Ethereum Is Scaling
Of the three transitions Vitalik mentions, the rollup transition is at the most advanced stage. According to L2Beat, rollups see 5.12 times the number of transactions the main Ethereum chain sees. Just one year ago, rollups hardly ever surpassed the number of transactions processed in the main chain.
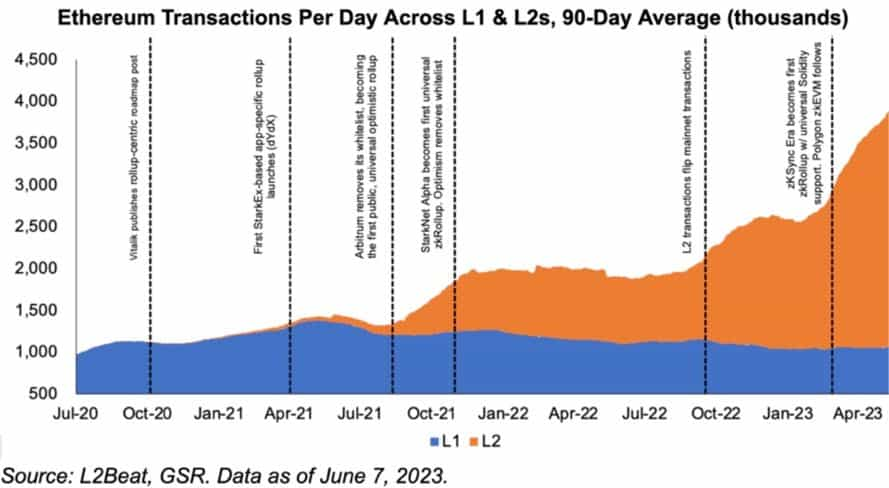
Everything points towards rollup adoption increasing even further, with the following points being the main catalysts:
- An increasing number of DApps are choosing to launch on rollups to cater to the masses.
- More rollups, including Scroll, Coinbase’s Base, and Fraxchain - Frax Finance´s L2.
- Ethereum shard chains lowering rollup fees even further by a factor of 20+.
- Progress on inter-L2 communication and bridging.
2 – The Crypto Wallet Security Transition. Everyone Moving to Smart Contract Wallets
Vitalik sees the transition to smart contract wallets as another crucial step for Ethereum. Without it, he fears users may feel uncomfortable storing their funds (and non-financial assets) in Ethereum, hindering adoption and encouraging custodial solutions instead of self-storage.
This viewpoint arises from the understanding that current popular wallet solutions can often be cumbersome, difficult to use, and need more protection against theft and loss. As a result, it can become a hurdle for blockchain adoption.
Fortunately, a promising alternative is on the horizon: a newer type of smart contract wallet known as a "social recovery wallet." These wallets offer the potential for enhanced security and significantly improved usability compared to previous options. In another blog post, Vitalik expressed how they can contribute to his vision of the value proposition of blockchains:
“The whole point of digital technology, blockchains included, is to make it easier for humans to engage in very complicated tasks without exerting extreme mental effort or live in constant fear of making mistakes.” - Vitalik Buturin
The Crypto Wallet Landscape Today and its Issues
Currently, most Ethereum users utilize "externally owned accounts" (EOAs). These are simple cryptographic key pairs, with the public key serving as the account's address and the private key used to sign transactions. Most hardware and software wallets, such as Ledger or MetaMask, are EOAs.
The main problem with EOAs is that if the private key is lost, the assets in the account can become irretrievable. To mitigate this risk, many wallets use a mnemonic seed phrase. This is a 12 to 24-word encoding of the wallet's root private key. If a wallet is lost but the mnemonic phrase is retained, the user can input this phrase when setting up a new wallet. This action recovers the account, as the mnemonic phrase contains the root key from which all other keys can be derived. Although mnemonic phrases offer protection against loss, they are a cumbersome solution as they require keeping safe.
Social Recovery Crypto Wallets Offer Key Advantages
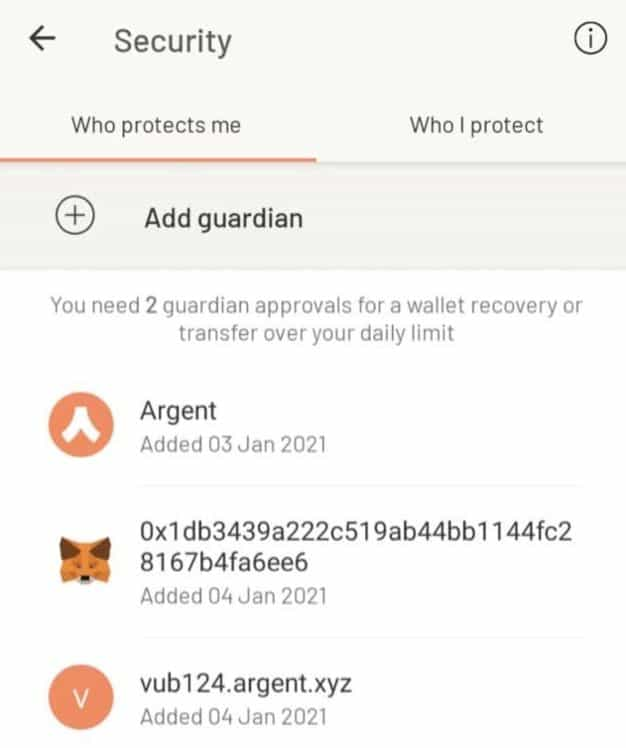
These wallets use a system where trusted contacts or devices known as guardians can help users regain access to their wallets if they lose their private key or other account access credentials. Social recovery wallets typically work as follows:
When setting up a social recovery wallet, the user selects his guardians. These guardians can be individuals the user trusts, secondary devices owned by the user, or third-party services. The user may need to approve these guardians from within the wallet, where adding a guardian can be as simple as typing in their ENS name or ETH address. Depending on his security needs and social circle, the user can also select as many guardians as he wishes. Vitalik favours a number of 7+ guardians for increased security, however, this may not be practical for most, as not everyone has that many Ethereum users among friends and family.
If the user loses access to their wallet, they can initiate a recovery process. This typically involves contacting the guardians and requesting they approve a recovery action. Once enough guardians approve the recovery action, wallet access can be regained. This might include generating a new private key, linking a new device, or another activity that re-establishes the user's control over their wallet. The number of guardians needed to approve recovery is usually set during wallet setup, where it is typical to require a majority. For instance, if a user has 7 guardians, at least 4 would have to approve the recovery action.
So, overall, social recovery wallets meet Vitalik’s three criteria for wallet design success:
- No Single Point of Failure: Even if an attacker gains access to one element, whether the user's device or private key, they can only take complete control of the wallet if they compromise the guardians. This drastically reduces the risk of theft.
- Low Mental Overhead: Unlike traditional wallets, losing a private key doesn’t mean permanently losing access to the wallet's contents, thanks to guardian recovery. Users don’t have to adopt new habits like mnemonic phrase custody or constantly remember to follow specific behavioral patterns – the mental effort required to use the wallet is minimal. The user can also select as many or as few guardians as they like, providing flexibility according to his personal risk tolerance and trust network.
- Maximum Ease of Transacting: Social recovery wallets offer maximum user-friendliness and simplicity in day-to-day operations. The user can use their social recovery wallet like a regular EOA wallet like Metamask, signing messages with their signing key so that each transaction signed can fly off with a single confirmation click.
It's worth noting that social recovery wallets come with their challenges. The user must trust their chosen guardians, and the recovery process can be slower and more complex than simply entering a backup phrase. However, social recovery wallets align with the strengths of human nature, as we are highly sociable creatures. As Vitalik quotes:
“The human brain is quite poorly suited for remembering passwords and tracking paper wallets, but it's an ASIC for keeping track of relationships with other people.” - Vitalik Buturin
Another advantage of smart contract wallets is the possibility of account abstraction. This means that some of the complexities of interacting with the Ethereum network, like gas management, can be handled at the contract level rather than by the end user. This makes for a smoother user experience by supporting more advanced features like transaction batching, gas payment in tokens other than Ether, and integration with other smart contracts for the automatic execution of complex transaction sequences.
3 – The Privacy Transition. Making Transfers and Gadgets Privacy-Preserving
According to Vitalik, the privacy transition is crucial for Ethereum's success because the default model of having all transactions available is a significant privacy sacrifice for many users. If Ethereum fails to address this issue, users may opt for centralized solutions that offer some data privacy.
Vitalik understands that transparency is a double-edged sword in the current blockchain landscape.
On the one hand, it provides unparalleled security and trust, offering an immutable ledger of transactions that everyone can verify. On the other hand, this same transparency could dissuade many users due to privacy concerns. Therefore, achieving a privacy transition is of paramount importance for Ethereum. It is a process that encompasses the ability to make funds transfers private and ensures that emerging features like social recovery mechanisms, identity protocols, and reputation systems are privacy-preserving.
In the blog post, the rudimentary activity of paying for a coffee (or a green tea if you have Vitalik’s taste buds) illustrates an average user's potential future use of Ethereum. However, we will need to solve critical challenges for Ethereum to be practical for micropayments. While you're here, check out our article that explores the future of Ethereum.
When I buy my morning iced americano to crack on with an article for the Coin Bureau blog, I don’t want the merchant to be able to trace the origin of those funds and be able to see my token holdings (even if mediocre) or any personal data I may have associated to my wallet. In my personal view, for micropayments to become mass-adopted, the payment experience must be as convenient as contactless card payment, and privacy assurances must also be in place.

Vitalik discusses Stealth address protocols as the proposed solution for enabling privacy on the Ethereum network. In essence, Stealth addresses create unique addresses for each transaction instead of a user having a single static address. Stealth addresses give the same privacy properties as a user generating a new address for each transaction but without requiring any interaction from the user.
Vitalik believes a basic stealth address scheme can be implemented relatively quickly today and could significantly boost practical user privacy on Ethereum. However, some work on the wallet side is required.
Will Ethereum Activity Ever Be Private? Some Regulatory Considerations
Out of all transitions, privacy is the greatest laggard. Today, most activities, such as transfers, DeFi, and Gaming, happen in non-privacy-enabled frameworks. A simple use-case such as paying for a coffee via decentralized rails seems distant. But we also have to ask ourselves: Will it ever be legal to pay for a coffee using privacy-enabled decentralized infrastructure? Is it even a good idea in the first place?
My opinion is that the answer to both questions is probably not. Today, banking requires KYC to comply with AML laws. This is in place to prevent money laundering and decrease the likelihood of getting away with crime. The same standards are beginning to be applied to cryptocurrency exchanges and other blockchain-based financial services. While privacy is a legitimate concern for many users, authorities will want to be able to track and audit transactions when necessary to discourage crime and make sure nobody can hide from the taxman.
In fact, privacy systems are already under regulators’ crosshairs. On Aug. 8, 2022, the U.S. Treasury Department barred customers in the U.S. from using Tornado Cash, a decentralized mixer protocol that enables private transactions on Ethereum. This is why I believe that day-to-day payments on Ethereum will never be fully private and will be handled by systems with a component of centralization.
It's important to remember that privacy doesn't necessarily mean complete anonymity. Users should have control over their personal information and who gets to see it. This is where privacy-preserving solutions can play a significant role. They can allow users to keep their transaction data confidential while also maintaining the ability to provide sufficient information to comply with law enforcement.
Does this mean that Ethereum will fail?
“Without the third (the privacy transition), Ethereum fails because having all transactions (and POAPs, etc.) available publicly for literally anyone to see is far too high a privacy sacrifice for many users, and everyone moves onto centralized solutions that at least somewhat hide your data.” - Vitalik Buterin
Well, this may depend on one’s vision of Ethereum. If we build systems that are more efficient, accessible, and support the free movement of decentralized assets, I wouldn’t call Ethereum failing, even if those systems involve a component of centralization to comply with AML laws.
In conclusion, while the idealistic goal of fully anonymous, decentralized transactions for everyday activities like buying coffee may not be feasible or desirable due to regulatory and practical concerns, the privacy transition still needs to be a critical part of Ethereum's evolution. By finding a pragmatist balance of privacy with accountability and providing users with control over their data, privacy-preserving technologies can help to make Ethereum more secure, user-friendly, and enable mass adoption.
It Gets Tricky: Each Transition Makes the Others More Complex.
So far, we have covered the benefits of the three transitions and their progress. Ethereum activity is becoming increasingly L2-centred, Smart contract wallets are growing in popularity, and privacy is a work in progress. The three transitions are on the way, no doubt, but there is a catch.
Each transition makes the other two more challenging to implement. The complexity of each change is not additive but multiplicative when we resolve them all at once because of the way they intertwine. A high degree of technical proficiency and coordination is required for a smooth implementation. In many ways, how we interact with the Ethereum network has to be re-invented, all while improving the accessibility for regular users.
Re-imagining 1 user = 1 address
We live in a world with numerous L2s. A user that has transacted in, for instance, Arbitrum, Optimism, and ZKSync will have accounts for all networks. With externally owned accounts, keeping the same address across all mainstream L2s is possible.
However, with the adoption of smart contract wallets, maintaining a consistent address across different Layer 2 solutions becomes more challenging. Most smart contract wallets are designed in such a way that the address depends on the smart contract's code, which can differ between Layer 1 and Layer 2 networks. While there have been efforts to create systems where the smart contract code and, thus, the address can be kept consistent across different networks, these solutions could be better and can create additional complexities. Moreover, with the privacy transition, the notion of consistent addresses across networks is complicated further if we use stealth addresses.
One thing becomes abundantly clear as the Ethereum network undergoes these three transitions. The "one user equals one address" paradigm weakens – users will own multiple addresses across multiple networks. This shift challenges the traditional relationship between user and blockchain, and consequently, the concept of an address that used to represent us users on-chain will have to change radically. Two engineering problems emerge:
- Wallets, as we know them today, must change: More information will be required to interact with other wallets, and gathering the necessary information will become more complex. Social recovery must also be re-imagined for a world with multiple wallets. Wallets will no longer be an ETH address; they would have to include, in some form, some combination of multiple addresses on numerous L2s, stealth meta-addresses, encryption keys, and other data.
- Certain apps and secondary infrastructure will require updating: Apps that rely on the assumption that address ownership is immutable must find other ways of achieving their goals.
Crypto Wallets, As We Know Them Today, Must Change
To understand why wallets as we know them must change, let’s start with the most basic example of a case where one has to acquire user information - transferring funds in a world with multiple L2s.
In a post-transition world, users shouldn’t have to deal with the multiple L2s that may exist. To see what I mean, see Vitalik’s MetaMask wallet below.
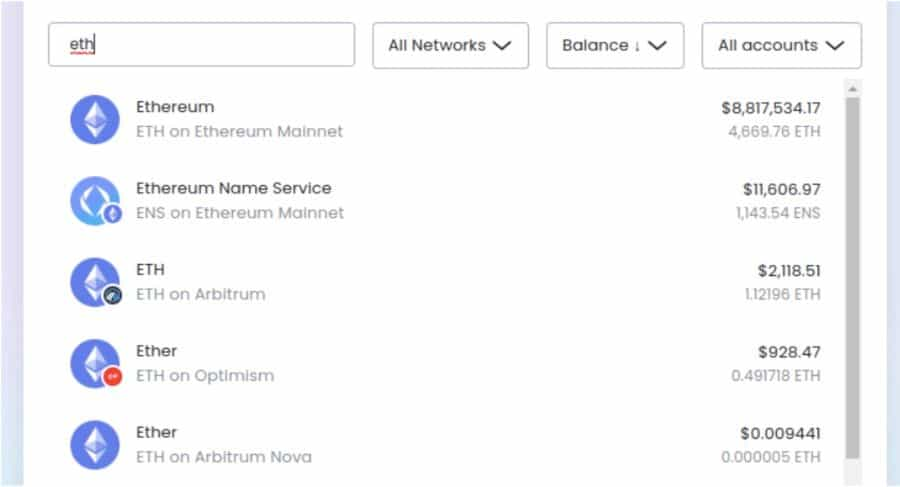
In one of his wallets, Vitalik has ETH in Ethereum, Arbitrum, Optimism, and Arbitrum Nova. If we have numerous L2s in 2023, imagine the number of l2s in 2030. Dealing with so many networks individually will not be reasonable for even the most tech-savvy.
The user is better off not having to deal with the idea of what blockchain infrastructure he is using altogether, similar to how we browse the internet without thinking about the protocols that power it. We could solve this issue by designing a wallet that shows an aggregated view of a user’s assets and works in one of the following ways Vitalik describes (or a combination of both).
- Receiving wallets (which could be merchants but also regular individuals) try to support every L2 and have some automated functionality for consolidating funds asynchronously.
- The recipient provides their L2 alongside their address, and the sender's wallet automatically routes funds to the destination L2 through some cross-L2 bridging system.
Here we see the first complexities emerge; simple actions like paying someone requires much more information than just an address. Even more is necessary if we also include privacy schemes like stealth addresses. Instead of simply needing an address to send someone money, you would need two pieces of information, a spending pubkey, and an encryption pubkey.
The resulting system is one where instead of sending money to an address through a particular network, you send it in a much more private and secure way through the most convenient network. These changes can significantly improve privacy and usability for Ethereum users but also add complexity. Wallets and other tools will need to adapt to handle these new requirements.
How a Crypto Wallet of The Future May Look Like
As well as supporting multiple networks and addresses, the wallet of a post-transition Ethereum should have social recovery functionalities.
Social recovery in a world where a user has multiple, sometimes unknown, addresses must be implemented to maintain privacy and keep gas costs low. Vitalik describes an architecture that solves the issues associated with social recovery in a multi-address world. This architecture is even more complex, and wallets must radically change. Still, it can also solve many problems associated with the three transitions in a neatly packaged manner.
The solution revolves around each user having a keystore contract. The keystore contract exists in a specific L2 or mainnet, and the verification logic of every other user-owned address in any network points to it. There are multiple ways that the keystore contract will be implemented, all with their unique tradeoffs, but they all share the same overarching idea.
In this architecture, transacting from one of the addresses requires a proof going into the keystore contract showing the current spending public key. Running social recovery on the keystore contract can change the owner structure on all networks at once. To maintain privacy, encryption and ZK-SNARKS can be utilized. A similar alternative architecture may allow the smart contract wallet on the source chain to control or receive assets on connected accounts.
While complex, this architecture may be a neat solution to multiple address social recovery and the requirement of more information to transact introduced earlier. We can package stealth meta-addresses, encryption keys, user identity information, and others into the keystore contract. The contract could contain information about you and how to interact with you and could become the primary identifier, acting as today’s address or ENS. Moreover, we could even use these wallets to recover encryption keys linked to decentralized Identity systems.
The Keystone contract architecture may be the go-to wallet of Ethereum that enables the three transitions, but there are additional engineering problems to solve.
Dapps and Secondary Infrastructure Will Require Updating
A new wallet architecture, L2-centric activity, and Privacy considerations mean that certain vital apps and infrastructure used today will need to be updated. Vitalik discusses a handful of examples:
One example is DApps, which currently depend on users providing off-chain signatures. With EOAs, this is a simple process. However, with the transition to smart contract wallets, the ERC-1271 standard needs to be adopted to provide a standardized way of handling this task. Despite this, many DApps still do not support ERC-1271 and will need to adjust.
Another area that needs rethinking involves DApps that use "Is this an EOA?" logic to differentiate between users and contracts. Currently used to prevent transfers or enforce royalties, this will not be compatible with smart contract wallets. As such, applications will likely need to rely less on preventing transfers and more on alternative techniques, like Harberger taxes.
How wallets interact with spending and encryption keys will need to improve. In the current ecosystem, wallets often use deterministic signatures to generate application-specific keys. Still, this method is "opaque" to the wallet, preventing it from implementing user-interface-level security checks. In a more mature ecosystem, wallets will have to explicitly handle functionalities such as signing, encryption, and related processes. This could reduce scams and phishing attacks.
Lastly, light clients, such as Helios, need to evolve. Light clients are specialized programs designed to interact with the blockchain without downloading the entire ledger. Currently, these clients validate Layer 1 (L1) headers and verify Merkle branches of the L1 state and transactions rooted in the L1 header using a light client sync protocol. However, as Ethereum continues to evolve and Layer 2 scaling becomes more prominent, these light clients will have to adapt and start verifying not only the L1 but also the Layer 2 (L2) state. In the future, they will need to verify proofs of the L2 state that are rooted in the state root stored in the L1. A more advanced version of this process might involve looking at L2 pre-confirmations.
ENS: A Success Story in Adapting to Ethereum's Transitions
While the technical challenges are significant, we have already seen successful adaptation stories emerge. One such example is the Ethereum Name Service (ENS). The ENS team recognized the need for adaptation early, especially considering the potential for skyrocketing transaction fees in the face of another bull market. Recognizing the potential impact on ENS usage, especially for decentralized social media use cases where users demand nearly free registration, the ENS team took proactive steps to make ENS work on L2.
The ENS's successful adaptation to Ethereum's "Three Transitions" indicates that such radical reforms are possible. It serves as a guiding light for other applications and infrastructures in the Ethereum ecosystem, demonstrating that aligning with these transitions is achievable with the right approach and forward-thinking strategies.
The Future Is Bright for Ethereum, but Full of Challenges
Ethereum is evolving from a cumbersome technology used by a few tech-savvy people to a platform for the masses, like the internet in the late 90s. Current engineering problems are not just about technical feasibility but about actual accessibility for regular users and require unprecedented coordination.
Vitalik believes that to solve these challenges, it may be helpful to start thinking explicitly about L1 + cross-L2 support, wallet security, and privacy as necessary basic features of the ecosystem stack rather than building each of these things as addons that can be designed separately by individual wallets.
I do not doubt that with the brilliance and ingenuity of the Ethereum community, the challenges will be solved, and we will come closer to Vitalik’s vision of Ethereum to bring a global and permissionless experience to the average user.
While you're here, check out some of our Ethereum-focused content:
- Ethereum Dominance: ETH vs. Other Blockchains
- How to Use Ethereum: Surfing Ethereum Transactions
- Unifying Ethereum: Abstraction & Interoperability
- What are Testnets? Ethereum Testnets Explained!
- Best Ethereum Wallets: Top 10 Options for Secure ETH Storage!
- Best ETH Staking Pools in 2024: Where to Stake Ethereum!
Frequently Asked Questions
The three major transitions identified by Ethereum founder Vitalik Buterin are:
- The Layer 2 (L2) scaling transition
- The wallet security transition
- The privacy transition
The L2 scaling transition involves the adoption and integration of Layer 2 solutions, specifically rollups. Rollups are smart contract-enabled frameworks built on Ethereum that significantly increase transaction capacity by processing computations off the main Ethereum chain (Layer 1) and returning compressed results.
The wallet security transition emphasizes the shift to smart contract wallets, particularly those with social recovery functionalities. This transition aims to enhance security, usability, and privacy for users, addressing issues associated with traditional externally owned accounts (EOAs) and their susceptibility to loss.
Ethereum plans to address transaction fees and scalability through the adoption of Layer 2 solutions, specifically rollups. Rollups process transactions off the main Ethereum chain, significantly reducing costs. They offer a more scalable and cost-effective alternative, with fees expected to decrease further with the introduction of Ethereum shard chains.
The ENS team recognized the need for adaptation early and proactively made ENS work on Layer 2 solutions to address potential issues with high transaction fees. The successful adaptation of ENS serves as a positive example for other applications and infrastructures in the Ethereum ecosystem.
Disclaimer: These are the writer’s opinions and should not be considered investment advice. Readers should do their own research.


